Did you get hit by Bianlian ransomware? Don’t panic. We’re here to help. This page contains information and statistics about Bianlian ransomware decryption, removal, and recovery. Read on to find out more, or get in touch with us now and for a FREE assessment of your situation.
How do I know if Bianlian Ransomware has infected my system?
The Bianlian ransomware started gaining visibility in 2022, proving their ability to effectively exploit security vulnerabilities and encrypt data.
Bianlian quickly made a shift in a lot of cases to extortion for data leaks instead of encrypting data.
Bianlian operates on the Ransomware as a Service Model, meaning it is run by a specialized team which licenses its software to franchises and takes a 10% commission for every successful attack. The creators of Bianlian promise regular code updates free of charge to help the affiliate members carry out successful ransomware attacks.
What should I do when my data has been encrypted by Bianlian Ransomware?
As in any virus attack, you need to do whatever necessary to stop the spread of the virus. Shut down your computer or server normally and disconnect all network connections immediately, including any data storage devices and online cloud storages. For more details please read our free guide to ransomware response.
It’s not advisable to try to pay the ransom on your own. In our experience, professional negotiators are consistently able to achieve much better results. We keep records on the various ransomware groups so that we understand their modus operandi, and we calibrate our negotiations accordingly.
It’s also advisable to have IT professionals handle data recovery. If not properly handled, it is possible to lose data in the recovery process. Our team of German technicians has an excellent track record of recovering 100% of client data.
Keep calm! Contact us, and we can help you!
BIANLIAN RANSOMWARE STATISTICS & FACTS
Diverse groups use Bianlian ransomware, so ransom amounts may vary.
The average Bianlian ransom amount is somewhere between $100,000 – $350,000. If you purchase Bitcoin to pay this, you will need to add 10% to cover the quick-buy method fees if you are purchasing with a credit card or PayPal on an exchange.
The Bianlian ransomware downtime can we longer than average ransomware incidents. This is because most Bianlian attackers use a chat interface or email to communicate and there is no automated way to make a payment.
Depending on your company size and how often you use IT-systems in your daily business, this is the most expensive part of this incident. Additional to the unavailability of your IT-systems, this is damaging your company reputation.
Your goal should be to get your systems back to a productive state as soon as possible. The best way to do this is to call in experts, which have a vast knowledge of Bianlian ransomware and get the IT-systems back up running.
There is a high chance of getting a working Bianlian decryptor after paying the attackers. But there’s never a guarantee.
Some attackers have a good reputation for providing working Bianlian decryptors. Others are known scammers and will never provide one.
The most common attack vector for Bianlian ransomware is spam emails and contagious webpages.
| Bianlian RANSOMWARE SUMMARY | |
|---|---|
| Name | Bianlian Virus / Bianlian Ransomware |
| Danger level | Very High. Advanced Ransomware which makes system changes and encrypts files |
| Release date | 2022 |
| OS affected | Windows & Linux ESXI |
| Appended file extensions | .bianlian |
| Ransom note | Look at this instruction.txt |
| Contact email address | [email protected] |
| Tox Messenger | A4B3B0845DA242A64BF17E0DB4278EDF 85855739667D3E2AE8B89D5439015F07E81D12D767FC |
HOW TO IDENTIFY BIANLIAN RANSOMWARE
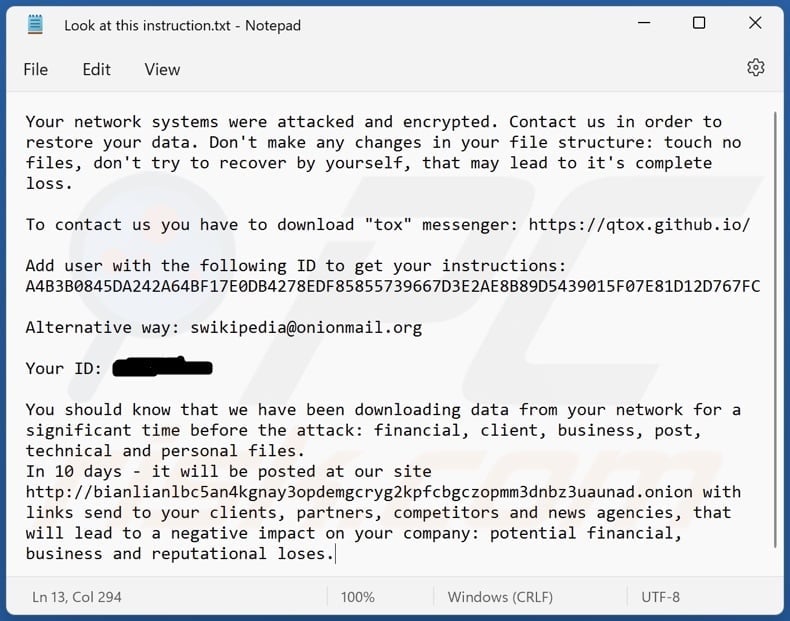
This is an average Bianlian ransomware note.
Your network systems were attacked and encrypted. Contact us in order to restore your data. Don’t make any changes in your file structure: touch no files, don’t try to recover by yourself, that may lead to it’s complete loss.
To contact us you have to download “tox” messenger: hxxps://qtox.github.io/
Add user with the following ID to get your instructions:
A4B3B0845DA242A64BF17E0DB4278EDF 85855739667D3E2AE8B89D5439015F07E81D12D767FCAlternative way: [email protected]
Your ID: –
You should know that we have been downloading data from your network for a significant time before the attack: financial, client, business, post, technical and personal files.
In 10 days – it will be posted at our site hxxp://bianlianlbc5an4kgnay3opdemgcryg2kpfcbgczopmm3dnbz3uaunad.onion with links send to your clients, partners, competitors and news agencies, that will lead to a negative impact on your company: potential financial, business and reputational loses.
Bianlian attackers usually leave a txt file with the name “Look at this instruction.txt” and contains all the necessary information you will need to contact the attackers and get your data back.
It’s usually safe to open this file, just be sure the full file extension is *.txt
FREQUENTLY ASKED QUESTIONS
The only way to know precisely how much ransomware response will cost is to contact us for a free consultation.
Ransomware response cost varies according to the type of attack, how much data is affected, the number of computers infected, and your local environment (computer performance, servers, operating systems). The response includes removal of the ransomware, negotiations with attackers and transferring payment if necessary, restoring data, patching the vulnerability that led to the attack, and preparing all documentation for legal compliance and insurance claims. The course of action our clients choose also affects the overall cost.
The minimum cost for small companies generally starts around several thousand euros, including the cost of the ransom. However, if at all possible, we strongly recommend avoiding paying the attackers. Paying the attackers encourages them to harm more people. However, if it is not economically feasible, we handle fully legally compliant payments to attackers. The overall expense depends a lot on the ransom amount demanded, and how successful negotiations are. We maintain a database on ransomware gangs to negotiate more effectively. In some cases, negotiations can result in a significant reduction in the ransom payment.
We have a greater than 98% success rate.
In the case of most of our clients who have cyber insurance, their coverage pays the cost of our services, as well as the ransom, if necessary.
- Professional ransomware response can significantly decrease downtime. We deal with hundreds of cases every year. Through our years of experience, we have developed a streamlined process that brings our clients back online as fast as possible. In the event that a ransom has to be paid, purchasing the necessary cryptocurrency can take days. The process of resolving a ransomware attack without prior experience can take many hours of research. Most of our cases are completely resolved 24-72 hours after we begin the recovery process.
- Avoid dealing with criminals and ensure legal compliance. Most companies don’t feel comfortable dealing with cyber-criminals. It can add another layer of stress in emergency. We maintain files on different groups of hackers in order to maximize security and effectiveness of negotiations. We also ensure that all communications and transfers comply with applicable laws and regulations to protect our clients against potential legal problems.
- Cryptocurrency transfers. It is always better to avoid giving into the attacker’s demands. If backups and normal recovery methods fail, however, there may be no other choice. Most ransomware attackers demand payment in Bitcoin. We guide you through the whole process of creating a crypto currency wallet and buying the crypto currency with you. Therefore we have different cooperation partner in order to prepare your wallet and do the transaction as quick and easy as possible for you.
- Ensure data integrity and security. As specialists in the field of ransomware incident response, we are always refining industry best practices for data recovery. We have robust, standardized procedures for backing up encrypted data, restoring data, and removing viruses to ensure that there is no data loss or damage.
- Easy Insurance Reporting: All of our clients receive a detailed incident report with all information required by cyber-insurance and for law enforcement purposes. Thankfully, cyber-insurance often covers the cost of cyber-extortion as well as professional ransomware response services. Completing all paperwork correctly from the beginning can speed up the process of filing a claim and recovering lost funds.
- Backup, Backup, Backup! In most cases, a fresh and secure backup of data can prevent ransomware attack from succeeding. For this reason, many attackers put in a lot of effort to find and encrypt backups. The best backup will be air-gapped, meaning physically disconnected from your main network. It is also important to have a regular backup schedule with robust security procedures.
- Install a Next-Gen Antivirus. Next generation anti-virus software combines a classic signature-based antivirus with powerful exploit protection, ransomware protection and endpoint detection and response (EDR). Mcafee, Fireeye, and Sentinel One are all examples of antivirus software with these features.
- Install a Next-Gen Firewall. A Next-Gen-Firewall is also called Unified threat management (UTM) firewall. It adds a layer of security at every entry and exit point of your company data communication. It combines classic network security with intrusion detection, intrusion prevention, gateway antivirus, email filtering and many other features.
If you can afford it, having staff or hiring a dedicated service to monitor network traffic can also help to detect unusual activity and prevent ransomware attacks. Ransomware attackers usually do a lot of surveillance on a network before attempting a hack. This “reconnaissance” phase has certain tell-tale signs. If you can catch these early, it’s possible to detect the attacker early and deny them access to the network.
If you get hit by ransomware, a professional ransomware recovery service can help to identify and patch security gaps.
BeforeCrypt is founded, established, licensed and registered in Germany as an GmbH business with worldwide operations. We have a full-time team of staff, contractors and cybersecurity consultants ready to work with you round the clock.
Although based in Germany, our support is available 24/7 and in 20 languages. You can use our contact form here to submit a ransomware ticket.
We are always happy to assist our clients and get them back up and running in minimal time as possible.
In emergencies, we can start with the ransomware data recovery immediately. Since our support team operates 24/7, we can reduce your downtime to a minimum by working non-stop to recover your data.
Need fast help with Bianlian ransomware recovery? Contact us now and get instant help from ransomware experts



