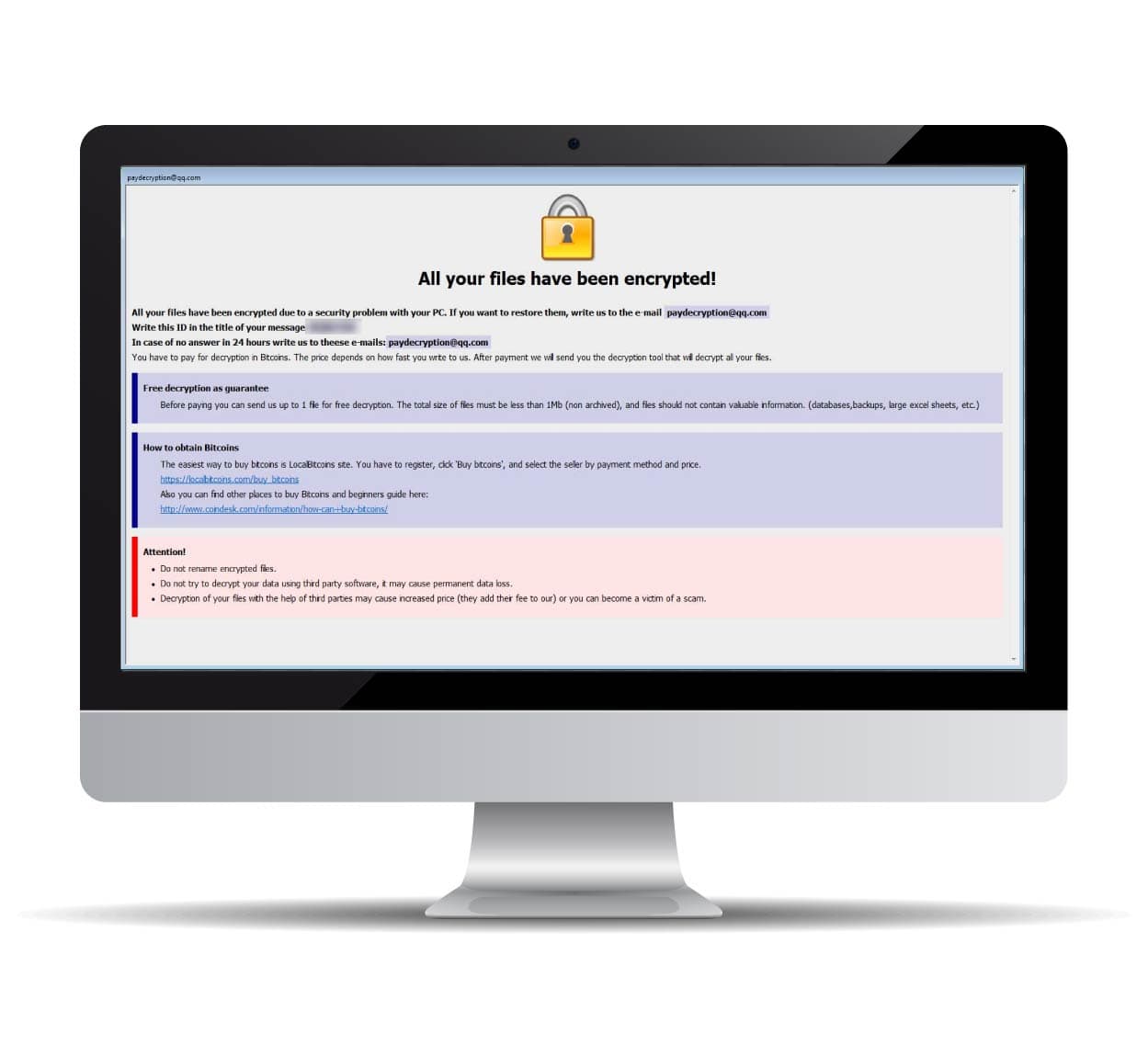
As a company or as a IT-service provider, dealing with a ransomware attack is an emergency situation. You may be wondering how the cyber attackers got into the network, whether they were able to steal data or how you can efficiently recover the encrypted data.
As a first step please shut down your computer or server as usual and disconnect all network connections immediately, including any data storage devices and online cloud storage. As soon as you contact us, you will receive a detailed guide on how best to proceed in the first 24 hours after an attack, completely free of charge.
Do not pay the ransom or try to remove the ransomware trojan on your own. You should leave the removal of ransomware, and the subsequent recovery of your valuable company data to experts.
BeforeCrypt is here to help you as a serious and highly-effective partner in case of a ransomware attack. Thanks to our experience and knowledge from more than 1500 successful ransomware recoveries, in most cases we can recover 100% of your encrypted data.