6 benefits from preparing for a ransomware attack



The Challenge
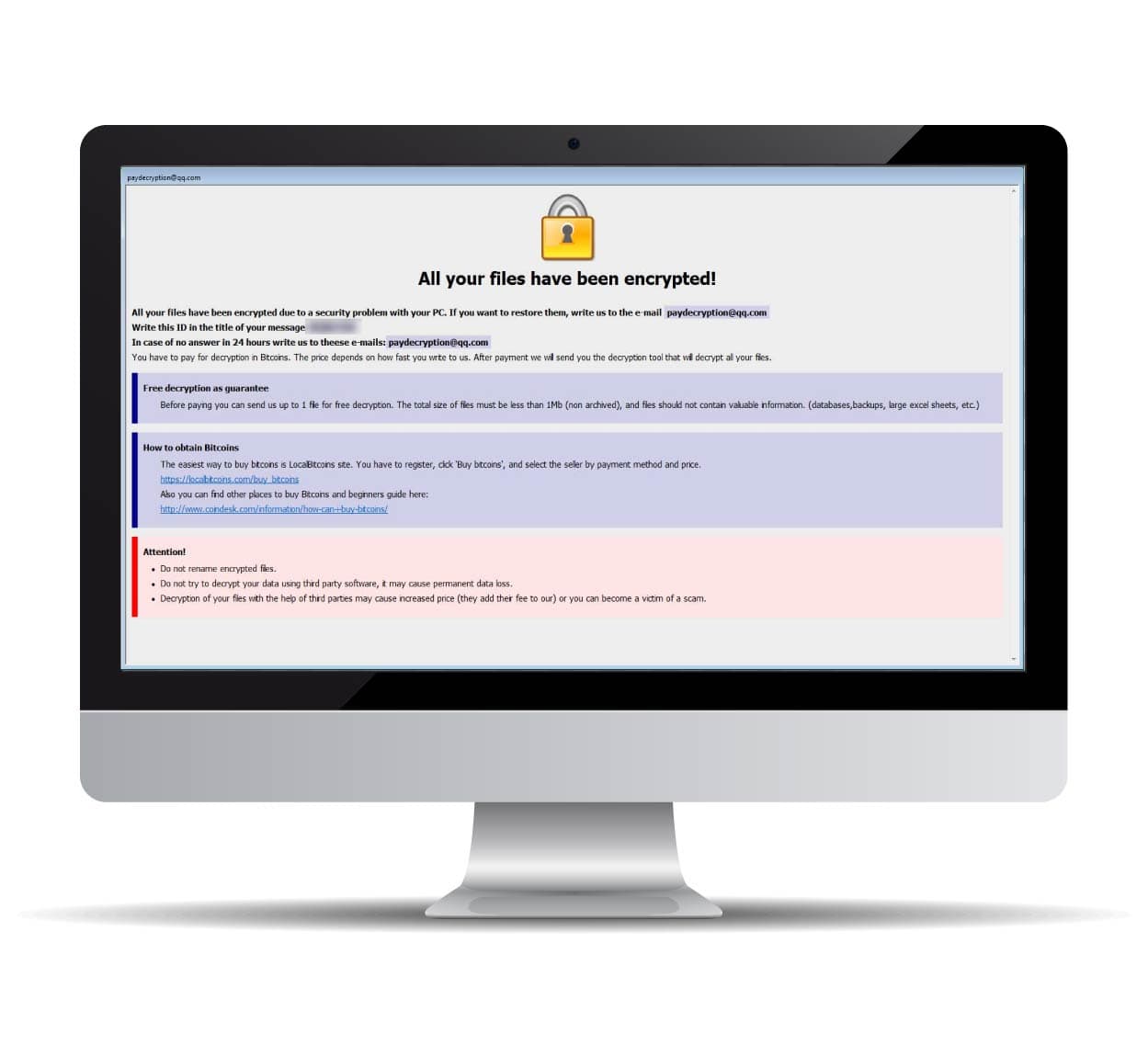
In recent years, the number of cyber attacks with ransomware deployment on enterprises has increased dramatically. The damage caused by the loss of operations and the release of stolen corporate data runs into billions of dollars worldwide.
Even in the best secured large enterprises, there are always negative headlines, as the cyber attackers penetrate the companies by exploiting vulnerabilities (e.g. zero day exploits), e-mail phishing or even through inside jobs. In our recent Forbes article, we described the growth and dangers of ransomware in more detail.
In almost all of today’s cyber attacks, ransomware incidents in particular pose the greatest threat to companies. When such an emergency occurs, it is often necessary to call in additional experts, as the internal IT department or IT service providers are not fully familiar. They lack the specialized knowledge of the particular ransomware variant, the calm and safe handling in an emergency, and the experience in negotiating ransoms with cyber extortionists. Cyber attackers almost always demand payment of ransoms in popular cryptocurrencies (e.g., Bitcoin or Monero). This poses daunting challenges for companies, especially when raising high 5- or 6- and 7-figure ransom sums.
If there is no other way out than to respond to the ransom demand, extensive compliance checks become necessary in order not to finance intentionally sanctioned persons/groups (keyword: financing of terrorism and anti-money laundering laws)
The Solution
This is why we have developed the BeforeCrypt Ransomware Incident Response Retainer. We prepare your company step-by-step for a cyber attack and are available 24/7 thanks to a guaranteed SLA.
In the first step, we prepare an individual risk assessment. This consists of a comprehensive risk dialog followed by an analysis of the technologies used. You then receive a report with vulnerabilities in order to proactively reduce the attack vectors.
Based on the information available to us, we develop an individual Ransomware Disaster Recovery Plan for you. We clarify critical issues in advance (such as whether ransoms will be paid in the event of an emergency) and prepare cryptocurrency exchange accounts for currency purchase.
Ransomware Incident Response Retainer Onboarding
Evaluate
STEP 1
- ❯ Risk Assessment of the company
- ❯ Risk Dialogue with the company management
- ❯ Report with action steps to proactively reduce attack vectors
- ❯ Renewed risk assessment every 6-12 months
Prepare
STEP 2
- ❯ Customized Ransomware Disaster Recovery Plan
- ❯ Prepare Cryptocurrency Purchase (OTC)
- ❯ Onboarding 24/7 On-Duty Emergencies Hotline
- ❯ Cyber-Attack Incident Management Coaching
Recover
STEP 3
- ❯ Determine ransomware variant & exploring recovery options
- ❯ Evaluate your risk based on historical incident insight
- ❯ Professional ransom negotiation (If necessary)
- ❯ Ransom Settlement and subsequent decryption of the systems
Report
STEP 4
- ❯ Incident report for law enforcement & insurance
- ❯ GDPR compliance check & reporting
- ❯ Sanctions compliance program checks for ransom payments
- ❯ Best-practice security recommendations to avoid reinfection
Case Studies From Our Customers
Problem
The entire network was encrypted due a ransomware-attack over the weekend and it was unclear, how to deal with this emergency situation.Solution
BeforeCrypt immediately advised the customer about legal requirements, removed the ransomware, reduced the ransom through professional cyber-attacker negotiation, provided ransom settlement and restored the customer network and data.
Result
Thanks to the professional ransomware incident support, operations could be restored within 48 hours. The data has been decrypted and the company is fully operational again. Also the customer avoided legal problems and costly self-made mistakes.

Simone Naletto
“The service provided by Before Crypt exceeded our most optimistic expectations from the point of view of the full recovery of compromised data and also in terms of seriousness and post event support. We have no hesitation in recommending this company.” ★★★★★
Cesvitem Onlus Non-profit Association – www.cesvitem.org
Phone: (+39) 41 5700843

Rupert Hamader
“Super uncomplicated quick assistance and also quick, fast, competent deployment of the technicians. Processing went very quickly. Would like to give 10 instead of 5 stars.” ★★★★★
Hamader IT – www.hamader.it
Phone: (+43) 699 12 66 0000
Problem
Although the customer network was optimally protected against cyber attacks, hackers exploited an unknown security gap and this resulted in encryption upon the entirety of customer data. Since there was no internal expert with knowledge in regards to ransomware, the IT service provider was looking for a firm with expertise.
Solution
BeforeCrypt gave professional incident advice, handled negotiations with the extortionists and the legally compliant ransom settlement, so the IT service provider was fully able to focus on the internal restore.
Result
Together we were able to restore the customer network within 72 hours. Also we closed the open security gap and avoided another incident through the implementation of an extended backup strategy and an emergency plan.
Problem
A large ransomware attack hit a hotel group with over 30 locations. Hotel services fully ceased to operate, over 650 employees were partially unable to work. A fast recovery from backups was impossible and the cyber-attackers had most likely stolen company data.
Solution
The management hired experts as soon as possible in order to avoid more damage and restore operations quickly. BeforeCrypt took on the leading role and coordinated the customer’s internal IT department, took care of ransomware compliance issues and guided the customer through an efficient and secure process and took the lead over the communication with the cyber-attackers.
Result
With the help of BeforeCrypt, the requested ransom was reduced by 75.000 Euro, fortunately the ransom had not to be paid. By restoring the services and re-entering a manageable amount of lost data the downtime of operations was drastically reduced. The analysis of the firewall communication revealed no unduly high data upload so all critical compliance requirements were met.

Thomas Koch
“Full recommendation for BeforeCrypt. A huge help for us as medium-sized companies, even though we had a backup strategy – previously found to be good – that turned out to be unsuitable for ransomware. Now we can concentrate on our core business again.” ★★★★★
Phone: (+49) 30 609 86 45 20

Omar Apostol
“At first ,I had a few hesitations because of the working location between Asia and Europe but after signing the contract and estimation. I felt their professionalism and sincerity on their promise. They never stopped until they recovered all the files that are necessary to our company. Thank you very much BeforeCrypt – Jeff, Christian, Benjamin and Janos – Thank you very much from the bottom of my heart.” ★★★★★
Singapore Takada Industries PTE LTD – www.takada.com.sg
Phone: (+65) 6861 3666

Philipp Diethelm
“From the first second we felt that we were in good hands. Very fast reaction and response times regardless of office hours, as well as coordinated and uncomplicated cooperation with us and our IT specialists. BeforeCrypt had extensive knowledge of the attacker group and their methods and helped us plan the next steps. Full recommendation & trust!” ★★★★★
Diga Möbel AG – www.diga.ch
Phone: (+41) 44 802 10 10

Maximilian Madile
“I can recommend BeforeCrypt’s service to anyone who has been the victim of Ransomware. The got in touch quickly, are very knowledgeable and their professional standars seemed state of the art. We didn’t get to work with them in the end for a variety of (internal) reasons but I have no reason to doubt that my experience would have been anything less than satisfactory.” ★★★★★
Madile Group Real Estate – www.madile.at
Phone: (+43) 463 218 180
Europe's Leading Ransomware Experts
At BeforeCrypt, we are committed to providing exceptional support for ransomware incidents. In these difficult situations, our expert knowledge provides peace, security and trust … But don’t just take our word for it.

Why Choose BeforeCrypt Ransomware Recovery Services?
Benefit directly from our experience from over 1.000 successful Ransomware incidents.
FREQUENTLY ASKED QUESTIONS
The only way to know precisely how much ransomware response will cost is to contact us for a free consultation.
Ransomware response cost varies according to the type of attack, how much data is affected, the number of computers infected, and your local environment (computer performance, servers, operating systems). The response includes removal of the ransomware, negotiations with attackers and transferring payment if necessary, restoring data, patching the vulnerability that led to the attack, and preparing all documentation for legal compliance and insurance claims. The course of action our clients choose also affects the overall cost.
The minimum cost for small companies generally starts around several thousand euros, including the cost of the ransom. However, if at all possible, we strongly recommend avoiding paying the attackers. Paying the attackers encourages them to harm more people. However, if it is not economically feasible, we handle fully legally compliant payments to attackers. The overall expense depends a lot on the ransom amount demanded, and how successful negotiations are. We maintain a database on ransomware gangs to negotiate more effectively. In some cases, negotiations can result in a significant reduction in the ransom payment.
We have a greater than 98% success rate.
In the case of most of our clients who have cyber insurance, their coverage pays the cost of our services, as well as the ransom, if necessary.
- Professional ransomware response can significantly decrease downtime. We deal with hundreds of cases every year. Through our years of experience, we have developed a streamlined process that brings our clients back online as fast as possible. In the event that a ransom has to be paid, purchasing the necessary cryptocurrency can take days. The process of resolving a ransomware attack without prior experience can take many hours of research. Most of our cases are completely resolved 24-72 hours after we begin the recovery process.
- Avoid dealing with criminals and ensure legal compliance. Most companies don’t feel comfortable dealing with cyber-criminals. It can add another layer of stress in emergency. We maintain files on different groups of hackers in order to maximize security and effectiveness of negotiations. We also ensure that all communications and transfers comply with applicable laws and regulations to protect our clients against potential legal problems.
- Cryptocurrency transfers. It is always better to avoid giving into the attacker’s demands. If backups and normal recovery methods fail, however, there may be no other choice. Most ransomware attackers demand payment in Bitcoin. We guide you through the whole process of creating a crypto currency wallet and buying the crypto currency with you. Therefore we have different cooperation partner in order to prepare your wallet and do the transaction as quick and easy as possible for you.
- Ensure data integrity and security. As specialists in the field of ransomware incident response, we are always refining industry best practices for data recovery. We have robust, standardized procedures for backing up encrypted data, restoring data, and removing viruses to ensure that there is no data loss or damage.
- Easy Insurance Reporting: All of our clients receive a detailed incident report with all information required by cyber-insurance and for law enforcement purposes. Thankfully, cyber-insurance often covers the cost of cyber-extortion as well as professional ransomware response services. Completing all paperwork correctly from the beginning can speed up the process of filing a claim and recovering lost funds.
- Backup, Backup, Backup! In most cases, a fresh and secure backup of data can prevent ransomware attack from succeeding. For this reason, many attackers put in a lot of effort to find and encrypt backups. The best backup will be air-gapped, meaning physically disconnected from your main network. It is also important to have a regular backup schedule with robust security procedures.
- Install a Next-Gen Antivirus. Next generation anti-virus software combines a classic signature-based antivirus with powerful exploit protection, ransomware protection and endpoint detection and response (EDR). Mcafee, Fireeye, and Sentinel One are all examples of antivirus software with these features.
- Install a Next-Gen Firewall. A Next-Gen-Firewall is also called Unified threat management (UTM) firewall. It adds a layer of security at every entry and exit point of your company data communication. It combines classic network security with intrusion detection, intrusion prevention, gateway antivirus, email filtering and many other features.
If you can afford it, having staff or hiring a dedicated service to monitor network traffic can also help to detect unusual activity and prevent ransomware attacks. Ransomware attackers usually do a lot of surveillance on a network before attempting a hack. This “reconnaissance” phase has certain tell-tale signs. If you can catch these early, it’s possible to detect the attacker early and deny them access to the network.
If you get hit by ransomware, a professional ransomware recovery service can help to identify and patch security gaps.
BeforeCrypt is founded, established, licensed and registered in Germany as an GmbH business with worldwide operations. We have a full-time team of staff, contractors and cybersecurity consultants ready to work with you round the clock.
Although based in Germany, our support is available 24/7 and in 20 languages. You can use our contact form here to submit a ransomware ticket.
We are always happy to assist our clients and get them back up and running in minimal time as possible.
In emergencies, we can start with the ransomware data recovery immediately. Since our support team operates 24/7, we can reduce your downtime to a minimum by working non-stop to recover your data.

