Has Dharma Ransomware held your company’s files hostage? If files have encrypted with a .DHARMA extension and backups failed, it is a highly critical situation. Do not hesitate, we’re here to help you. This page provides detailed information in regards to Dharma ransomware, decryption, recovery, removal and statistics. Contact us now to help you in recovering from a Dharma Ransomware Attack.
How do I know if our company has been hit with Dharma Ransomware?
A Dharma Encryption payload is a so-called Ransomware Trojan that encrypts an entire PC or a plethora if not all machines on your network. First discovered roundabout the 21st of October, 2017, Dharma Ransomware was originally known as Crysis and had a close relationship to XTBL. Once files are encrypted, hackers proceed to demand a bitcoin payment to remove the ransomware encryption.
There are over 30 variants of the virus with a number of file extensions such as .BMP, .BIP, and .COMBO among many others.
Just like most other ransomware variants, Dharma is most commonly spread via an open RDP (Remote Desktop Protocol) port, either through the use of various exploits and vulnerabilities inherent to Remote Desktop of through dictionary or brute force attacks. Once access is gained by the attackers, various methods are employed to spread laterally such as the use of Mimikatz to gain administrative access or control over more machines within the network. All the while the attackers poise themselves to launch their encryption at the opportune time whilst monitoring company activities to determine value and perfect their strategy.
What should I do when my data has been encrypted by Dharma Ransomware?
When Dharma Ransomware infects your system, there are a number of precautionary steps that you can take to avoid the spread of virus to other computers on the network.
For starters, turn off your systems and disconnect them from your network. While not a 100% guaranteed way of stemming the spread, this is a good way to help contain the incident.
For more details please download our Ransomware Response Emergency Guide.
Do not under any condition communicate or negotiate with the hackers. These hackers are very smart and will use all possible means to inflict damage upon you. Call in ransomware removal and recovery experts like BeforeCrypt to help you in recovering your data.
Unfortunately, in some cases the data is so precious, companies cannot afford to let it go. And in times like these, there is many times no option other than paying the ransom. This is where BeforeCrypt comes in. We affect a professional and diplomatic negotiation with the hackers, while making sure that the ransomware removal process is carried out under very controlled and secure circumstances. Leave this to us. We’ve been there, done that. We know how to deal with these cyber criminals and will help you in getting a dharma decryptor tool to safely recover your files after doing a proper dharma trojan removal.
BeforeCrypt can help you as a transparent and highly-ethical partner should you be infected by Dharma ransomware. Thanks to our experience and knowledge, we can recover 100% of your encrypted data in the vast majority of cases.
Keep calm! Contact us, and we can help you!
DHARMA RANSOMWARE STATISTICS & FACTS
The nature of a Dharma Ransomware attack is different depending on the hacker or hacker group behind the attack. This amounts to varying degrees of ransom amounts that each hacker or group charges.
The average Dharma ransom amount is somewhere between $2,000–$8,000. However, over the last year, the average amount has begun to exceed $8,000. In addition, approximately 10% of Bitcoin exchange fees will apply to the use of quick-buy methods such as PayPal or credit card.
The Dharma ransomware downtime is a bit longer than normal ransomware attacks. The manual process of email-based communication with the attackers can add a considerable delay in the response time.
Depending on your company size and how often you use IT-systems in your daily business, this is the most expensive part of this incident. Additional to the unavailability of your IT-systems, this is damaging your company reputation.
Your goal should be to get your systems back to a productive state as soon as possible. The best way to do this is to call in experts, which have a vast knowledge of Dharma ransomware and get the IT-systems back up running.
There is a high chance to get a working Dharma decryptor after paying the attackers. But there’s never a guarantee to get a working decryption key at all.
Depending on the file extension and email address of the attackers, there are different chances of getting a working Dharma decryptor after payment.
Some attackers have a good reputation for providing working Dharma decryptors. Others are known as scammers and will never give a Dharma decryptor.
The most common attack vector for Dharma ransomware is an unsecured RDP-Connection (Remote Desktop Protocol). Followed up by phishing emails and security vulnerabilities.
HOW TO IDENTIFY DHARMA RANSOMWARE
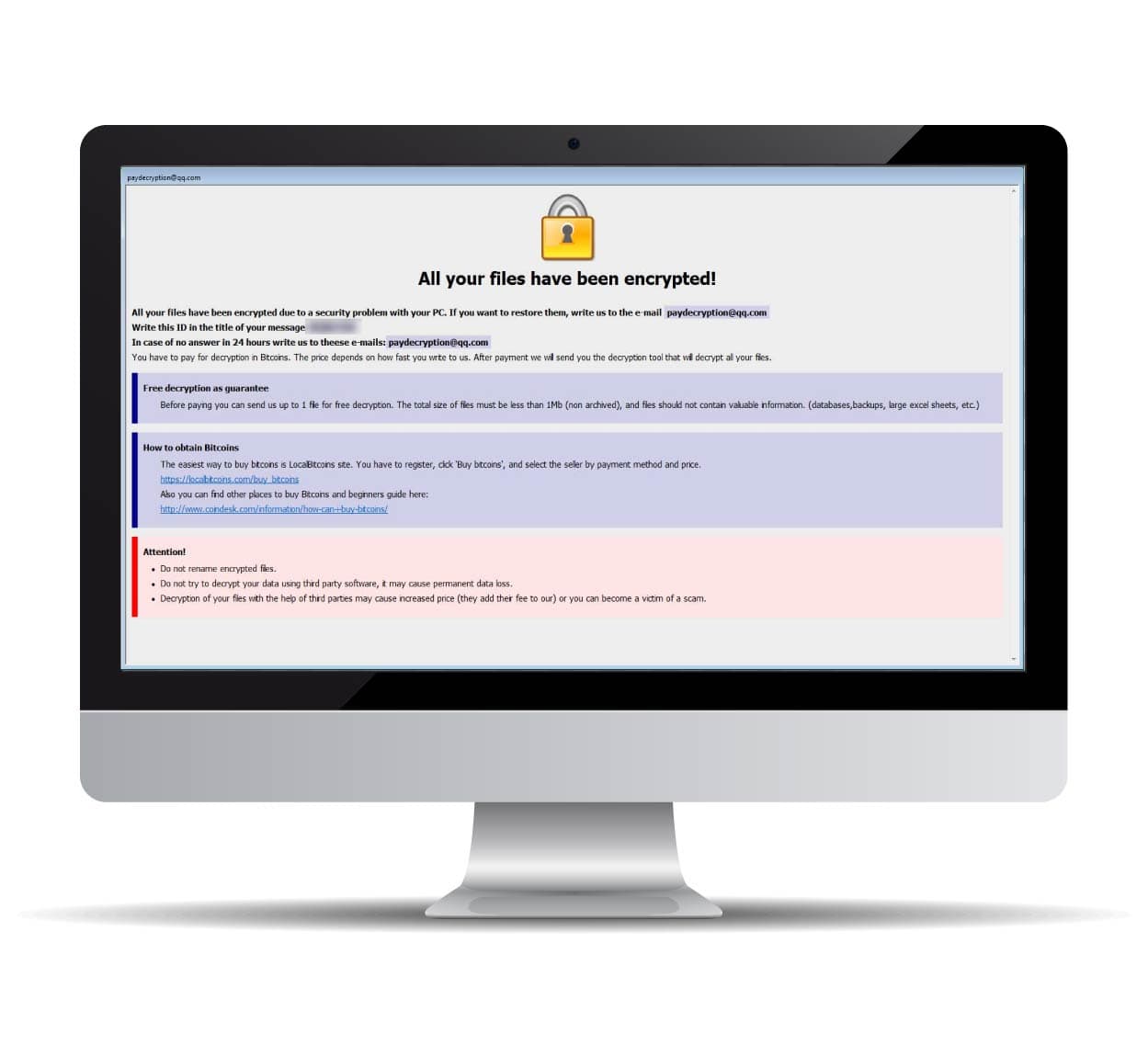
The first sign of a Dharma Ransomware attack is that you’ll receive a message, which has 4 different color coded sections.
Instructions (First Section):
This is the most alarming part of any ransomware attack. You get a notice that your system has been hacked and all files are encrypted. You will receive a unique ID of the Ransomware case that you’ll need to communicate to them through email.
Free Decryption as Guarantee (Second Section):
As a proof that their decryptor works, the second section talks about how the victim can send 1 file to decrypt for free. This is intended to assure the victim that they’ll get a working decryptor key to decrypt their data.
How to Obtain Bitcoins (Third Section):
No hacker in their right mind would provide their banking coordinates or they’d be traced instantly, right? In this section, the hackers provide a medium to pay the ransom by purchasing bitcoin and sending them to an indicated bitcoin address.
Attention (The Last Section)!
Needless to state, this section provides in reality the most accurate advice that you need to follow.
“Do not rename encrypted files” They are right. If you try to rename your files extension, they won’t be restored, instead you’ll lose the data.
“Do not try to decrypt your data using third party software. It may cause permanent data loss.” This is 100% correct also. Latest versions of Dharma Ransomware cannot be decrypted with any free and/or paid decryption tool. Any use of a decryption software can potentially destroy the ability of your files to be restored at a later date.
“Decryption of you files with the help of third parties may cause increased price (they add their price to our), or you can become the victim of a scam.” There are a number of unethical data recovery companies out in the wild disguising themselves as recovery experts, when they merely negotiate with the hackers without disclosing to you and have their share of the ransom. These companies only add fuel to fire and secretly collude with hackers in a highly unethical manner.

This is an average Dharma ransomware note.
All your files have been encrypted! All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail [email protected] Write this ID in the title of your message 000QQQ In case of no answer in 24 hours write us to theese e-mails:[email protected] You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files. Free decryption as guarantee Before paying you can send us up to 1 file for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.) How to obtain Bitcoins The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price. https://localbitcoins.com/buy_bitcoins Also you can find other places to buy Bitcoins and beginners guide here: http://www.coindesk.com/information/how-can-i-buy-bitcoins/ Attention! Do not rename encrypted files. Do not try to decrypt your data using third party software, it may cause permanent data loss. Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
This is another indication of a Dharma attack. Cutting the long story short, all they ask you to do is simply to send them an email. There are no instructions as it is just a simple plain text message.

All your data is encrypted!
for return write to mail:
[email protected] or [email protected]Almost always, there is a * .txt file in every folder that has been encrypted. The text file usually has the name “FILES ENCRYPTED.txt” or “RETURN FILES.txt” and contains all the necessary information to contact the Dharma Ransomware attackers to get your data back. It’s usually safe to open this file, just be sure the full file extension is *.txt.
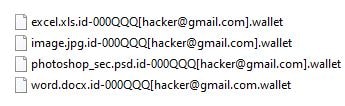
Sometimes the attackers leave the encrypted files without any Dharma ransomware notes. The file name contains a generic and customized ID number and the attackers’ email. This Dharma ID number is always individual, and sometimes there are additional IDs if more than one system got encrypted by Dharma ransomware. The appended file extensions depend on the Dharma ransomware variant. The most common ones are .java, .cesar, .cezar, .wallet, .dharma, .arrow, .write, .onion,.adobe, .btc, .pdf and .waifu.
DHARMA DECRYPTOR DEMONSTRATION
This is a technical demo of the Dharma Decryptor software. Copyright by BeforeCrypt.
FREQUENTLY ASKED QUESTIONS
- Professional ransomware response can significantly decrease downtime. We deal with hundreds of cases every year. Through our years of experience, we have developed a streamlined process that brings our clients back online as fast as possible. In the event that a ransom has to be paid, purchasing the necessary cryptocurrency can take days. The process of resolving a ransomware attack without prior experience can take many hours of research. Most of our cases are completely resolved 24-72 hours after we begin the recovery process.
- Avoid dealing with criminals and ensure legal compliance. Most companies don’t feel comfortable dealing with cyber-criminals. It can add another layer of stress in emergency. We maintain files on different groups of hackers in order to maximize security and effectiveness of negotiations. We also ensure that all communications and transfers comply with applicable laws and regulations to protect our clients against potential legal problems.
- Cryptocurrency transfers. It is always better to avoid giving into the attacker’s demands. If backups and normal recovery methods fail, however, there may be no other choice. Most ransomware attackers demand payment in Bitcoin. We guide you through the whole process of creating a crypto currency wallet and buying the crypto currency with you. Therefore we have different cooperation partner in order to prepare your wallet and do the transaction as quick and easy as possible for you.
- Ensure data integrity and security. As specialists in the field of ransomware incident response, we are always refining industry best practices for data recovery. We have robust, standardized procedures for backing up encrypted data, restoring data, and removing viruses to ensure that there is no data loss or damage.
- Easy Insurance Reporting: All of our clients receive a detailed incident report with all information required by cyber-insurance and for law enforcement purposes. Thankfully, cyber-insurance often covers the cost of cyber-extortion as well as professional ransomware response services. Completing all paperwork correctly from the beginning can speed up the process of filing a claim and recovering lost funds.
Depending on the variant of Dharma ransomware, it could be possible that there’s a publicly available decryption method. Please use our ransomware recovery request form, and we can check this for free for you.
But it is never a guarantee to completely recover Dharma ransomware files. The ransomware uses AES 256-bit and RSA 2048 encryption standards together to create strong encryption.
Depending on the Dharma variant, there are different types of Dharma decryptors. Dharma ransomware is based on a 2-way decryption process. You will receive a decryptor executable, mostly called “decryptor.exe”, which first is used to scan the entire computer, network drives, external HDDs and other removable devices. After this scan has finished, you get a “Request code”, this contains the public key request, and it is completely individual for each victim.
This “Request code” is sent over to the attackers, who then generate your decryption keys. The keys generated are unique for each person. A decryption key which you get from another victim, who has already received a Dharma decryption key, will not work for you.
Dharma ransomware creates multiple Windows registry entries, creates hidden executable files and sometimes opens a backdoor in firewalls for further access. There are multiple steps necessary, including the cleaning up of the Windows registry, scanning for malware and the manual cleanup of the Dharma ransomware. Depending on the system environment, it is sometimes safer and faster to reinstall the operating system.
Dharma Ransomware’s primary method of distribution is through the use of unsecured RDP (Remote Desktop Protocol), a port commonly used by employee and/or remote workers to access a company’s network remotely. Hackers use various methods to infiltrate the network via RDP, such as bruteforce attacks, phishing and port scanning.
Once the credentials are compromised, hackers gain access to the entire network, spread Dharma ransomware and eventually end up locking the entire network out of access for the company and their employees.
The problem with RDP is that it’s not safe, and Windows is notoriously known to feature an unsecure version of remote desktop protocol. Thousands of corporate RDP credentials are being sold on the dark web for as little as $3 per credentials.
- Backup, Backup, Backup! In most cases, a fresh and secure backup of data can prevent ransomware attack from succeeding. For this reason, many attackers put in a lot of effort to find and encrypt backups. The best backup will be air-gapped, meaning physically disconnected from your main network. It is also important to have a regular backup schedule with robust security procedures.
- Install a Next-Gen Antivirus. Next generation anti-virus software combines a classic signature-based antivirus with powerful exploit protection, ransomware protection and endpoint detection and response (EDR). Mcafee, Fireeye, and Sentinel One are all examples of antivirus software with these features.
- Install a Next-Gen Firewall. A Next-Gen-Firewall is also called Unified threat management (UTM) firewall. It adds a layer of security at every entry and exit point of your company data communication. It combines classic network security with intrusion detection, intrusion prevention, gateway antivirus, email filtering and many other features.
If you can afford it, having staff or hiring a dedicated service to monitor network traffic can also help to detect unusual activity and prevent ransomware attacks. Ransomware attackers usually do a lot of surveillance on a network before attempting a hack. This “reconnaissance” phase has certain tell-tale signs. If you can catch these early, it’s possible to detect the attacker early and deny them access to the network.
If you get hit by ransomware, a professional ransomware recovery service can help to identify and patch security gaps.
Need fast help with Dharma ransomware recovery? Contact us now and get instant help from ransomware experts