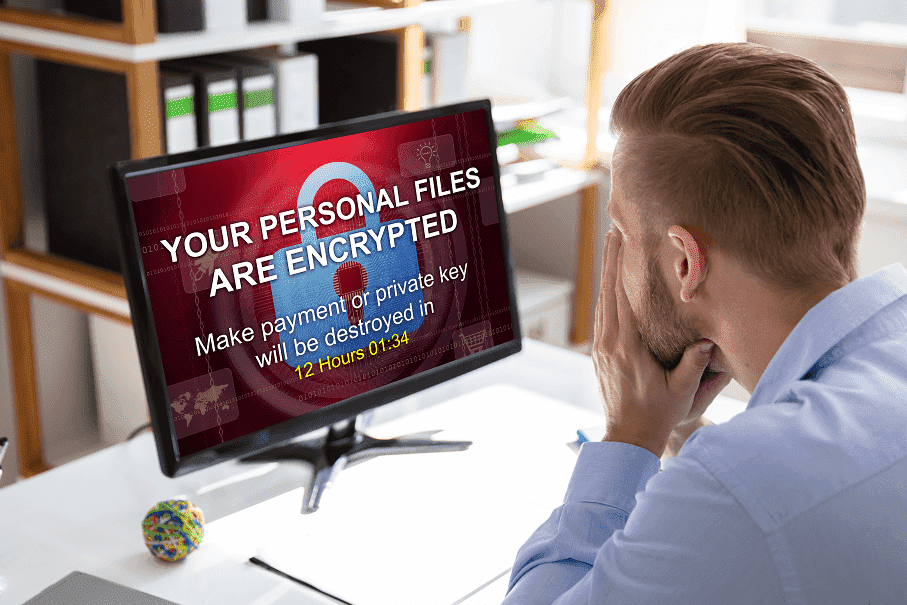
Have you been affected by the recent wave of ESXiArgs ransomware attacks? If so, it may be an emergency, but don’t panic. We are here to provide you with the necessary support for recovery and removal. Go through our detailed ransomware recovery process or get a FREE quote now.
Don’t wait before it causes more damage to your network.