As if getting extorted by ransomware hackers wasn’t bad enough, scammers are increasingly taking advantage of people’s desperation to cash in with fake decryptor tools. This is one reason why we always emphasize the importance of staying calm when faced with a ransomware attack. If you act while in a panic, it’s much easier for scammers to push you into making bad decisions.
It’s so evil, you would hardly expect it. I mean, who actually thinks about going and scamming people who have already been scammed? Not surprisingly, there is little or honor or morality among thieves. However, this is the grim reality of today’s internet.
Since these scams are spreading, it’s important to raise awareness about them.
Examples of Fake Decryptors
So what does a fake decryption scam look like?
One example that we ran into recently is using YouTube to advertise to potential victims. Posted by used “Ransomware Virus,” the video is titled “Phobos Ransomware Decrypt and Decryptor.” We won’t post the link here for security reasons.
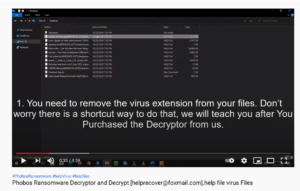
It shows what appears to be a Windows desktop environment infected with Phobos ransomware. The video goes through a process of changing the modified file extensions, and then runs a tool called “decryptor.exe”.
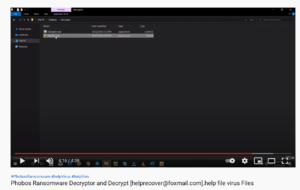
As if by magic, the files are suddenly restored!
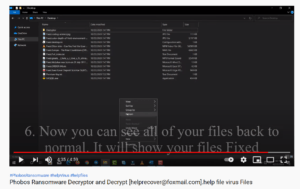
The only problem is that the tool doesn’t work as advertised. One of our clients recently fell victim to this scam, and lost over $5,000 to false promises by the scammers. This underscores the importance of consulting with professionals specialized in ransomware before trying to decrypt files on your own.
This isn’t the even the worst decryption scam out there. Another fake decryption tool was observed last year which encrypts the user’s files with another layer of ransomware. Talk about disappointment.
This variant, called Zorab, is marketed as a free decryptor for the STOP Djvu ransomware variant. STOP Djvu generally goes for mass infections of low value targets, asking for ransoms in the range of $500.
How to Spot Authentic Decryption Tools
There are a number of functional, free decryption tools in existence. It’s important to be careful to verify the source where you download these tools, however. Make sure that the site where you find them is reputable and well known, and beware any claims that sound “too good to be true.” Also, if anyone asks you for money, beware! All of the functional decryption tools we know of are offered for free.
Also, always be careful to double check the authenticity of URLs. We have not seen this tactic specifically, but hackers are known to sometimes create convincing copies of legitimate websites to distribute malware.
Avast, an antivirus company, has a list of freely available ransomware decryption tools on their website. Generally, well known and established brands like this will not put links to malicious downloads on their websites.
Working decryptors are usually very limited in terms of capabilities. For example, they usually only work with older versions of specific strains of ransomware. If anyone offers you a decryptor and claims it works for more than one ransomware variant, they’re probably a scammer.
The Moral of the Story: Beware of Easy Fixes
Unfortunately, it’s very common for people to think that there is a “magic bullet” which can make their problem disappear. This is just one more reason why it’s critical that everyone cultivate a better understanding of cybersecurity. The encryption used by most ransomware variants cannot be cracked at this point in time.
If you ever get infected by ransomware, you can always call us for a free consultation. We know about most of the free decryptors out there, and we can help you identify which ransomware variant infected your system. Once we know the exact type of ransomware, we will know if a free decryptor is available or not. For now, stay aware, and stay safe!








