Did you get hit by GlobeImposter 2.0 ransomware? Don’t panic. We’re here to help. This page contains information and statistics about GlobeImposter 2.0 ransomware decryption, removal, and recovery. Read on to find out more, or get in touch with us now and for a FREE assessment of your situation.
How do I know if GlobeImposter 2.0 Ransomware has infected my system?
The GlobeImposter ransomware started gaining visibility in August, 2017. In the following 4 years, the virus has caused huge amounts of damage across the US, Europe, Asia and Africa, impacting organizations of all sizes.
Globeimposter 2.0 is a prolific ransomware strain, accounting for over 4% of total ransomware infections in 2020. Globeimposter generally spreads through spam campaigns. It has caused a few notable attacks, including one which shut down a web hosting service, causing all of the sites it hosted to crash.
GlobeImposter operates on the Ransomware as a Service Model, meaning it is run by a specialized team which licenses its software to franchises and takes a 10% commission for every successful attack. The creators of GlobeImposter 2.0 promise regular code updates free of charge to help the affiliate members carry out successful ransomware attacks.
While there are a number of versions, BeforeCrypt is acquainted with 5 confirmed variants, including 726 (the original strain) and 792 (the re-released strain).
The blank slate spamming method is one of the most common ways used to spread GlobeImposter. Victims report receiving blank emails with a zip attachment. If they open the the zip file, the ransomware attack executes.
Globeimposter is also known to spread via torrent sites or pirated software and movies. \
What should I do when my data has been encrypted by GlobeImposter 2.0 Ransomware?
As in any virus attack, you need to do whatever necessary to stop the spread of the virus. Shut down your computer or server normally and disconnect all network connections immediately, including any data storage devices and online cloud storages. For more details please read our free guide to ransomware response.
It’s not advisable to try to pay the ransom on your own. In our experience, professional negotiators are consistently able to achieve much better results. We keep records on the various ransomware groups so that we understand their modus operandi, and we calibrate our negotiations accordingly.
It’s also advisable to have IT professionals handle data recovery. If not properly handled, it is possible to lose data in the recovery process. Our team of German technicians has an excellent track record of recovering 100% of client data.
Keep calm! Contact us, and we can help you!
GLOBEIMPOSTER 2.0 RANSOMWARE STATISTICS & FACTS
Diverse groups use GlobeImposter 2.0 ransomware, so ransom amounts may vary.
The average GlobeImposter 2.0 ransom amount is somewhere between $7,500 – $70,000. If you purchase Bitcoin to pay this, you will need to add 10% to cover the quick-buy method fees if you are purchasing with a credit card or PayPal on an exchange.
The GlobeImposter 2.0 ransomware downtime can usually be shorter than normal ransomware attacks. This is because most GlobeImposter 2.0 attackers use an automated TOR site to accept payment and deliver the decryption tool.
Depending on your company size and how often you use IT-systems in your daily business, this is the most expensive part of this incident. Additional to the unavailability of your IT-systems, this is damaging your company reputation.
Your goal should be to get your systems back to a productive state as soon as possible. The best way to do this is to call in experts, which have a vast knowledge of GlobeImposter 2.0 ransomware and get the IT-systems back up running.
There is a high chance of getting a working GlobeImposter 2.0 decryptor after paying the attackers. But there’s never a guarantee.
Some attackers have a good reputation for providing working GlobeImposter 2.0 decryptors. Others are known scammers and will never provide one.
The most common attack vector for GlobeImposter 2.0 ransomware is spam emails and contagious webpages.
| GLOBEIMPOSTER 2.0 RANSOMWARE SUMMARY | |
|---|---|
| Name | GlobeImposter 2.0 Virus / GlobeImposter 2.0 Ransomware |
| Danger level | Very High. Advanced Ransomware which makes system changes and encrypts files |
| Release date | 2017 |
| OS affected | Windows |
| Appended file extensions | .CRYPT, .PSCrypt, .FIX, .FIXI, nCrypt, .Virginlock, .keepcalm, .pizdec, crypted!, .write_us_on_email, .write_on_email, .write_me_[email], A1CRYPT, .hNcyrpt, .cryptall, .402, .4035, .4090, .4091, 452, .490, .707, .725, .726, .911, .cryptch, .ocean, .nopasaran, .s1crypt, .scorp, .sea, .skunk , .3ncrypt3d, .707, .medal, .FIXI, .TROY, .VAPE, .GRAF, .GORO, .MAKB, .HAPP, .BRT92, .HAIZ, .MORT, .MIXI, JEEP, .BONUM, .GRANNY, .LEGO, .RECT, .UNLIS, .ACTUM, .ASTRA, .GOTHAM, .PLIN, .paycyka, .vdul, .2cXpCihgsVxB3, .rumblegoodboy, .needkeys, .needdecrypt, .bleep, .help, .zuzya, .f1crypt, .foste, .clinTON, .ReaGAN, .Trump, .BUSH, .C8B089F, .decoder, .Uridzu, .f*ck, .Ipcrestore, .encen, .encencenc, .{[email protected]}BIT, [[email protected]].arena, .waiting4keys, .black, .txt, .doc, .btc, .wallet, .lock, .FREEMAN, .apk, .crypted_yoshikada@cock_lu (Yoshikada Decryptor), .crypted_zerwix@airmail_cc (Zerwix Decryptor), .suddentax, .XLS, .Nutella, .TRUE, TRUE1, .SEXY, .SEXY3, .SKUNK+, BUNNY+, .PANDA+, .ihelperpc, .irestorei, .STG, [[email protected]], .legally, .BAG, .bad, .rose, .MTP |
| Ransom note | HOW_OPEN_FILES.hta or how_to_back_files.html |
| Contact email address | [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected] |
HOW TO IDENTIFY GLOBEIMPOSTER 2.0 RANSOMWARE

This is an average GlobeImposter 2.0 ransomware note.
Your files are encrypted!
Your personal ID
***
All your important data has been encrypted. To recover data you need decryptor.
To get the decryptor you should:
pay for decrypt:
site for buy bitcoin:
Buy 1 BTC on one of these sites
1. https://localbitcoins.com
2. https://www.coinbase.com
3. https://xchange.cc
bitcoin adress for pay:
jlHqcdC83***:
Send 1 BTC for decrypt
After the payment:
Send screenshot of payment to [email protected] . In the letter include your personal ID (look at the beginning of this document).
After you will receive a decryptor and instructions
Attention!
• No Payment = No decryption
• You realy get the decryptor after payment
• Do not attempt to remove the program or run the anti-virus tools
• Attempts to self-decrypting files will result in the loss of your data
• Decoders other users are not compatible with your data, because each user’s unique encryption key
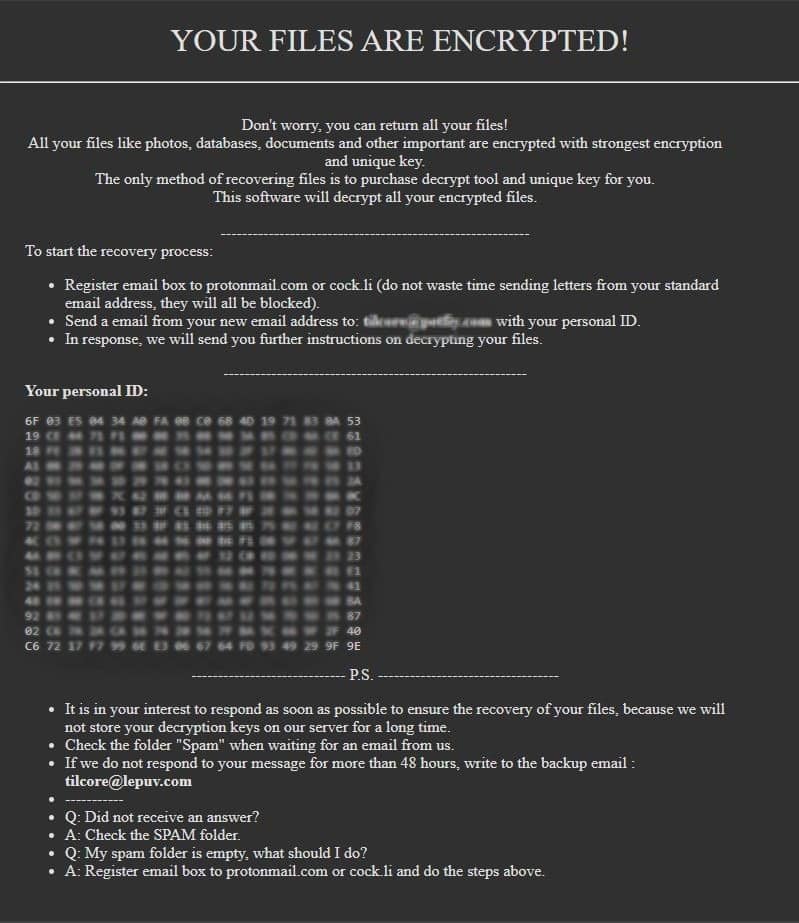
YOUR FILES ARE ENCRYPTED!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.———————————————————-
To start the recovery process:
Register email box to protonmail.com or cock.li (do not waste time sending letters from your standard email address, they will all be blocked).
Send a email from your new email address to: [email protected] with your personal ID.
In response, we will send you further instructions on decrypting your files.
———————————————————
Your personal ID:
<unique-ID>
—————————– P.S. ———————————-
It is in your interest to respond as soon as possible to ensure the recovery of your files, because we will not store your decryption keys on our server for a long time.
Сheck the folder “Spam” when waiting for an email from us.
If we do not respond to your message for more than 48 hours, write to the backup email : [email protected]
———–
Q: Did not receive an answer?
A: Check the SPAM folder.
Q: My spam folder is empty, what should I do?
A: Register email box to protonmail.com or cock.li and do the steps above.
GlobeImposter 2.0 attackers usually leave an HTML file with the name “how_to_back_files.html” and contains all the necessary information you will need to contact the attackers and get your data back. There are also chances when the same file is saved as a .txt file.
It’s usually safe to open this file, just be sure the full file extension is *.txt or *.html
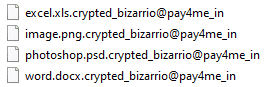
Sometimes the attackers leave the encrypted files without any GlobeImposter 2.0 ransomware notes. The file name will contain the attackers’ email. The appended file extensions depend on the GlobeImposter 2.0 ransomware variant. The most common ones are .bad; .BAG; .FIX; .FIXI; .legally;n .keepcalm; .pizdec; .virginlock[[email protected]]SON;
.[[email protected]]; .725; .ocean; .rose; .GOTHAM; .HAPP; .write_me_[[email protected]]; .726; .490; n.skunk
GLOBEIMPOSTER 2.0 DECRYPTER DEMONSTRATION
This is a technical demo of the GlobeImposter 2.0 Decryptor. Copyright by BeforeCrypt
FREQUENTLY ASKED QUESTIONS
Depending on the variant of GlobeImposter 2.0 ransomware, it could be possible that there’s a publicly available decryption method. Please use our ransomware recovery request form, and we can check this for free for you.
GlobeImposter 2.0 ransomware creates multiple Windows registry entries, creates hidden executable files and sometimes opens a backdoor in firewalls for further access. There are multiple steps necessary, including the cleaning up of the Windows registry, scanning for malware and the manual cleanup of the GlobeImposter 2.0 ransomware. Depending on the system environment, it is sometimes safer and faster to reinstall the operating system.
The most common attack vector for GlobeImposter 2.0 ransomware is spam emails and contagious webpages. It is mostly recognized by a zip file attachment in the email that has little to no context.
Globeimposter 2.0 ransomware has wreaked havoc across the globe by bringing down a number of corporate, government and business websites, and entire networks of companies.
GlobeImposter 2.0 ransomware encrypts files with an AES-256 bit algorithm. This algorithm, like most of those used by ransomware attackers, is currently impossible to break. There are currently no known free decryptors for GlobeImposter, which means that the only options are to restore from backup or negotiate with the attackers, preferably with a professional ransomware recovery team like BeforeCrypt.
- Professional ransomware response can significantly decrease downtime. We deal with hundreds of cases every year. Through our years of experience, we have developed a streamlined process that brings our clients back online as fast as possible. In the event that a ransom has to be paid, purchasing the necessary cryptocurrency can take days. The process of resolving a ransomware attack without prior experience can take many hours of research. Most of our cases are completely resolved 24-72 hours after we begin the recovery process.
- Avoid dealing with criminals and ensure legal compliance. Most companies don’t feel comfortable dealing with cyber-criminals. It can add another layer of stress in emergency. We maintain files on different groups of hackers in order to maximize security and effectiveness of negotiations. We also ensure that all communications and transfers comply with applicable laws and regulations to protect our clients against potential legal problems.
- Cryptocurrency transfers. It is always better to avoid giving into the attacker’s demands. If backups and normal recovery methods fail, however, there may be no other choice. Most ransomware attackers demand payment in Bitcoin. We guide you through the whole process of creating a crypto currency wallet and buying the crypto currency with you. Therefore we have different cooperation partner in order to prepare your wallet and do the transaction as quick and easy as possible for you.
- Ensure data integrity and security. As specialists in the field of ransomware incident response, we are always refining industry best practices for data recovery. We have robust, standardized procedures for backing up encrypted data, restoring data, and removing viruses to ensure that there is no data loss or damage.
- Easy Insurance Reporting: All of our clients receive a detailed incident report with all information required by cyber-insurance and for law enforcement purposes. Thankfully, cyber-insurance often covers the cost of cyber-extortion as well as professional ransomware response services. Completing all paperwork correctly from the beginning can speed up the process of filing a claim and recovering lost funds.
- Backup, Backup, Backup! In most cases, a fresh and secure backup of data can prevent ransomware attack from succeeding. For this reason, many attackers put in a lot of effort to find and encrypt backups. The best backup will be air-gapped, meaning physically disconnected from your main network. It is also important to have a regular backup schedule with robust security procedures.
- Install a Next-Gen Antivirus. Next generation anti-virus software combines a classic signature-based antivirus with powerful exploit protection, ransomware protection and endpoint detection and response (EDR). Mcafee, Fireeye, and Sentinel One are all examples of antivirus software with these features.
- Install a Next-Gen Firewall. A Next-Gen-Firewall is also called Unified threat management (UTM) firewall. It adds a layer of security at every entry and exit point of your company data communication. It combines classic network security with intrusion detection, intrusion prevention, gateway antivirus, email filtering and many other features.
If you can afford it, having staff or hiring a dedicated service to monitor network traffic can also help to detect unusual activity and prevent ransomware attacks. Ransomware attackers usually do a lot of surveillance on a network before attempting a hack. This “reconnaissance” phase has certain tell-tale signs. If you can catch these early, it’s possible to detect the attacker early and deny them access to the network.
If you get hit by ransomware, a professional ransomware recovery service can help to identify and patch security gaps.
Need fast help with GlobeImposter 2.0 ransomware recovery? Contact us now and get instant help from ransomware experts



