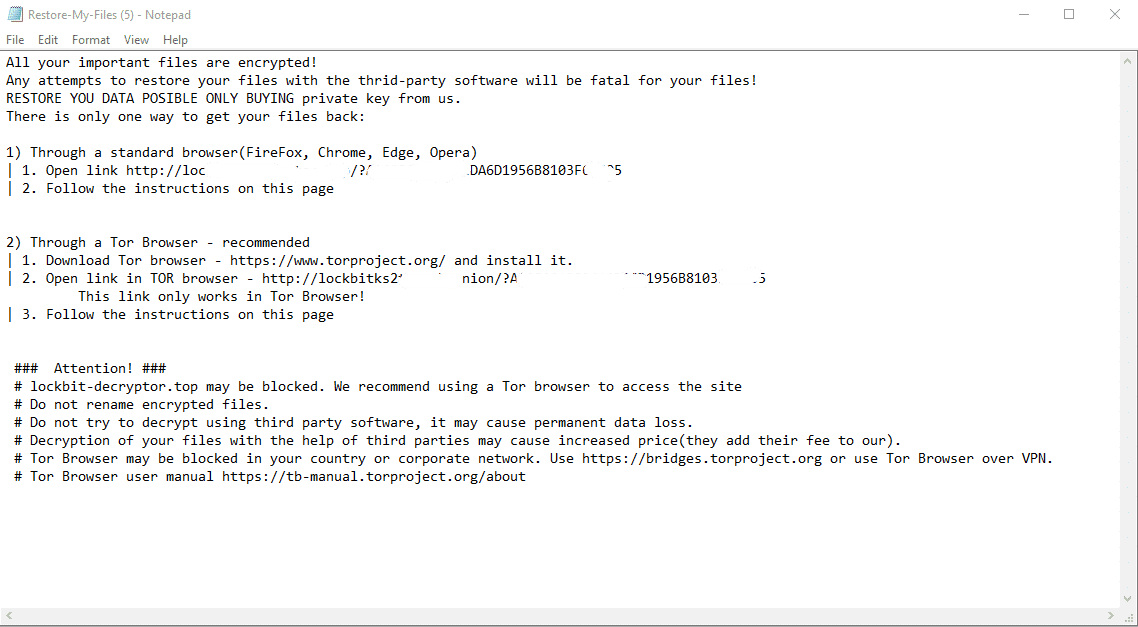
The only way to know precisely how much ransomware response will cost is to contact us for a free consultation.
Ransomware response cost varies according to the type of attack, how much data is affected, the number of computers infected, and your local environment (computer performance, servers, operating systems). The response includes removal of the ransomware, negotiations with attackers and transferring payment if necessary, restoring data, patching the vulnerability that led to the attack, and preparing all documentation for legal compliance and insurance claims. The course of action our clients choose also affects the overall cost.
The minimum cost for small companies generally starts around several thousand euros, including the cost of the ransom. However, if at all possible, we strongly recommend avoiding paying the attackers. Paying the attackers encourages them to harm more people. However, if it is not economically feasible, we handle fully legally compliant payments to attackers. The overall expense depends a lot on the ransom amount demanded, and how successful negotiations are. We maintain a database on ransomware gangs to negotiate more effectively. In some cases, negotiations can result in a significant reduction in the ransom payment.
We have a greater than 98% success rate.
In the case of most of our clients who have cyber insurance, their coverage pays the cost of our services, as well as the ransom, if necessary.