Has your network been infected by RYUK ransomware? Stay calm. We’re here to help. RYUK ransomware is one of the more prevalent strains of ransomware, and is know to affect organizations of all sizes. This page contains essential information and data about RYUK ransomware, decryption, removal, and recovery. Please review the information below or contact our support team now for a FREE consultation and get immediate help with RYUK ransomware recovery.
How do I know if RYUK has infected my system?
Operating since August 2018, the Russia-based criminal group SPIDER WIZARD is one of the most notorious and successful ransomware gangs active today. They are responsible for RYUK ransomware, which has hit major organizations like the Irish Health Service and health care infrastructure in the United States.
The group is also known for the “Trickbot” banking malware, which has targeted financial service providers worldwide. So far a wide assortment of organizations have fallen victim to RYUK, including multinational corporations, NGOs and governments.
What should I do when my data has been encrypted by RYUK Ransomware?
RYUK ransomware is usually used in highly targeted attacks on large organizations. Since these attacks are usually complex and involve penetrating multiple levels of security, the ransom demands are can be quite high, reaching millions of dollars.
If you get hit by RYUK ransomware, turn off your network immediately, and disconnect all drives, including external backup drives, from the network. For more details, take a look at our Complete Ransomware Response Guide.
We know of no free or paid decryptor tools for RYUK ransomware, but some dishonest actors have duped ransomware victims by claiming to have such tools. If someone claims to have a Ryuk decryption tool, beware. It’s very likely they are a scammer.
BeforeCrypt can help you resolve RYUK ransomware infections as quickly and effeciently, will full technical proficiency and legal compliance. We have extensive experience helping our clients recover 100% of their data, and our professional negotiators and detailed case files result in superior ransom reduction.
Keep calm! Contact us, and we can help you!
RYUK RANSOMWARE STATISTICS & FACTS
Since the victims of RYUK attacks are often enterprises and large organizations, the ransom amount is usually higher than with other ransomware variants.
However, these attackers have been known to demand different amounts based on the data they have on the organization. The average RYUK ransom amount is somewhere between $100,000–$350,000. However, in some cases, attackers have made demands as high as $800,000 to over $1 Million. If purchasing Bitcoin using quick-buy methods like credit card or PayPal, an additional 10% fee will be charged on top of this by cryptocurrency exchanges.
The downtime is longer than normal attacks due to the manual process of email-based communication with the attackers, which adds a considerable delay in the response time and data recovery process.
Since this is an enterprise-level attack, the longer your systems and files are held hostage, the costlier it will be in terms of PR damage. Your goal should be to get your systems back to productive state as soon as possible. The best way to do this is to call in experts like BeforeCrypt, who have a vast knowledge of this ransomware. We can help you in getting your network back up running.
There is a high chance to get a working RYUK decryptor after paying the attackers. But there’s never a guarantee to get a working decryption key at all.
It is in most cases either Remote Desktop Protocol or email Phishing are the 2 leading attack vectors. Unfortunately, even enterprises fail to secure their open RDP ports.
Due to an increase in remote working, a lot of employees now work from home using remote desktop control, leaving the company’s network exposed to hackers and all sorts of cyber criminals. But it isn’t limited to Remote Desktop Protocol.
In fact, the most common methods of this ransomware distribution is email phishing.
| RYUK RANSOMWARE SUMMARY | |
|---|---|
| Name | RYUK Virus / RYUK Ransomware / Cryptor 2.0 Ransomware |
| Danger level | Very High. Advanced Ransomware which makes system changes and encrypts files |
| Release date | August, 2018 |
| OS affected | Microsoft Windows |
| Appended file extensions | .ryk |
| Ransom note | RyukReadMe.txt, ReadMe.txt, UNIQUE_ID_DO_NOT_REMOVE.txt or RyukReadMe.html |
| Contact email address | [email protected]. [email protected], [email protected], [email protected], [email protected] |
HOW TO IDENTIFY RYUK RANSOMWARE

This is an average RYUK ransomware note.

Gentlemen!
Your business is in serious danger.
There is a significant hole in your company’s security system. We just entered your network.You should thank the Lord that you were hacked by serious people and not by stupid schoolboys or dangerous punks.
You can damage all your important data just for fun.Now your files are encrypted using the strongest military algorithms RSA 4096 and AES-256.
Nobody can help you recover files without our special decoder.Photorec, RannohDecryptor etc. repair tools are useless and can irrevocably destroy your files.
If you would like to restore your files, write an email to (Contacts are an the bottom of the leafes)
and attach 2-3 encrypted files (Each less than 5Mb, not archived and your files should not contain
valuable information (Databases, backups, large Excel data sheets, etc.).
You will receive decrypted samples and our conditions on how to get the decoder.
Don’t forget to write the framework of your company in the subject of your email.You have to pay for decryption in bitcoins. The final price depends on how quickly you write to us.
Every day of delay will cost you an additional +0.5 BT. Nothing personal, just businessAs soon as we get bitcoins, you will get back all of your decrypted data.
You will also receive instructions on how to close the vulnerability
and so you avoid such problems in the future
+ We recommend special software that makes hackers most troubled.Danger! Once again!
Do not rename encrypted files.
Do not try to decrypt your data with third party software.P.S. Remember, we are not cheaters.
We don’t need your files and information.
But after 2 weeks, your files and keys will be deleted automatically.
Just send a request right after the infection.
All data will be absolutely restored.
Your guarantee – decrypts samples.Contact emails
[email protected]
Or
[email protected]BTC wallet:
<unique-wallet>Ryuk
No system is secure
Almost always, there is a * .txt or *.html file in every folder that has been encrypted. The text file usually has the name “RyukReadMe.txt” or “RyukReadMe.html” and contains all the necessary information to contact the RYUK Ransomware attackers to get your data back. It’s usually safe to open this file, just be sure the full file extension is *.txt or *.html.
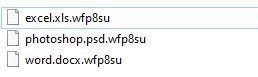
RYUK ransomware file names just show a different file extension. Unlike other ransomware variants, RYUK don’t includes an attacker email address or a unique ID in the filename.
RYUK DECRYPTOR DEMONSTRATION
This is a technical demonstration of RYUK Decryptor. Copyright by BeforeCrypt
RYUK RANSOMWARE ATTACK DEMONSTRATION
This is an average RYUK attack. Copyright by The PC Security Channel
FREQUENTLY ASKED QUESTIONS
RYUK ransomware, notoriously known for attacking corporations and large businesses, uses military grade encryption standards of AES 256 bit and RAS 1024 bit. Without the decryption key, it is impossible to decrypt large amounts of data. To get back up online in the shortest amount of time, the only resort left with victims is to pay the ransom amount.
The method of recovering data by restoring it from backups takes as much as up to weeks which isn’t viable for many corporations due to the costly business downtime.
Depending on the variant of RYUK ransomware, it could be possible that there’s a publicly available decryption method. Please use our request form, and we can check this for free for you. You can also use free websites to check this, too.
- Backup, Backup, Backup! In most cases, a fresh and secure backup of data can prevent ransomware attack from succeeding. For this reason, many attackers put in a lot of effort to find and encrypt backups. The best backup will be air-gapped, meaning physically disconnected from your main network. It is also important to have a regular backup schedule with robust security procedures.
- Install a Next-Gen Antivirus. Next generation anti-virus software combines a classic signature-based antivirus with powerful exploit protection, ransomware protection and endpoint detection and response (EDR). Mcafee, Fireeye, and Sentinel One are all examples of antivirus software with these features.
- Install a Next-Gen Firewall. A Next-Gen-Firewall is also called Unified threat management (UTM) firewall. It adds a layer of security at every entry and exit point of your company data communication. It combines classic network security with intrusion detection, intrusion prevention, gateway antivirus, email filtering and many other features.
If you can afford it, having staff or hiring a dedicated service to monitor network traffic can also help to detect unusual activity and prevent ransomware attacks. Ransomware attackers usually do a lot of surveillance on a network before attempting a hack. This “reconnaissance” phase has certain tell-tale signs. If you can catch these early, it’s possible to detect the attacker early and deny them access to the network.
If you get hit by ransomware, a professional ransomware recovery service can help to identify and patch security gaps.
Need fast help with RYUK ransomware recovery? Contact us now and get instant help from ransomware experts



