As part of our work in ransomware removal and prevention, we conduct detailed investigations into the methods used by ransomware gangs. The Sodinokibi ransomware gang, also known as REvil, is without a doubt one of the most prolific and effective groups currently active. By some estimates, it may be responsible for as many as 25% of all ransomware attacks conducted in 2020.
The gang is notable for executing a number of high profile attacks, and has received plenty of media attention. They made headlines by gaining access to private data of celebrities like Madonna, Lebron James, and even US President Donald Trump.
One of the main reasons for the Sodinokibi ransomware gang’s success is their organizational structure. They are known for pioneering the “ransomware as a service” (RaaS) model, in which a specialized team licenses out software to hackers in exchange for a percentage of profits. Sodinokibi is actively seeking to recruit talented hackers. Its recruitment process is not unlike that of a major software company’s sales department. They vet potential partners by reviewing their resumes, and contract out the dirty work of breaking into systems.
In the course of our research, we encountered one of Sodinokibi’s recruiting advertisements, pictured below. It contains some interesting information on the nature and scope of their operations.
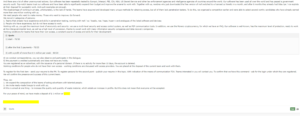
Tools Used by Sodinokibi Affiliates
We learn several things from their recruitment tactics. For one, their advertisements show that they are facing a shortage of skilled manpower, meaning they have no shortage of viable targets.
Some of the tools that they use include:
- Metasploit Framework (MSF)
- Cobalt Strike (CS)
- Koadic
All of these are penetration testing suites used to find vulnerabilities and inject exploits. This means it is worth checking whoever is in charge of your IT security, and make sure they are conducting regular penetration testing using similar software.
The ad also mentions Network Attached Storage (NAS) and Hyper Virtualization (Hyper-V). NAS is often used for maintaining backups, and are increasingly targeted in ransomware attacks. Backups are the first line of defense against ransomware attacks, so they are often a top priority for attackers.
You can enhance the security of your NAS by using a unique and secure username and password for administrator rights and enabling SSL. Another good practice is encrypting data stored in backups. Sodinokibi especially often threatens to release sensitive data to blackmail victims. If the data they access is encrypted, they will be unable to demand a second ransom.
Sodinokibi Ransomware’s Extraordinarily High Volume
Once affiliates break into a system, the Sodinokibi team handles communications and ransom payments themselves. That means their affiliates are only responsible for breaking into systems.
The advertisement offers incentives for the teams working for them; if they can generate more than $1 million in profit per week, the team responsible for the attack will get a discount on the fee taken by Sodinokibi central. IBM estimates that Sodinokibi’s overall revenues were at least $81 million in 2020, with the actual number very likely to be much higher.
Attracting Top Talent
Sodinokibi obviously enjoys media attention, calling major news outlets their “advertisers.” As more hackers use their software in high profile crimes, the media coverage builds up the reputation of the gang, attracting more talented hackers.
In order to further cultivate “talent,” the gang also holds competitions with prizes. These events serve to attract gifted individuals for recruitment, and to hone the skill set of their affiliates.
If the recruitment drive succeeds in finding more skilled hackers, it’s likely that Sodinokibi attacks will increase in 2021. This underscores the importance of understanding Sodinokibi’s method of operation and planning appropriate countermeasures.








