Hackers and cybercriminals have been turning their attention to big-game hunting, which basically refers to targeting bigger and more secure businesses where they can demand larger ransoms.
Big game hunting is usually carried out through spearfishing attacks. It’s a serious cybersecurity issue that has caused significant damage, service disruption, and at the same time crashing the stock price of giant corporations.
Spear phishing attacks have been the cause of some of the most serious and often quite expensive data breaches. According to the FBI’s 2018 Internet Crime Report, business email breaches cost businesses in the US $1.2 billion in 2018.
The number of Widenet RDP brute-force attacks is also on the rise, especially since March 2020 when COVID-19 quarantineshad been imposed worldwide. According to Kaspersky, the Russian cybersecurity firm, the number of RDP brute force attacks have skyrocketed across the globe as more people are forced to stay at home and companies deploy more RDP systems online.
The increased use of RDP has created a bigger realm of opportunity for hackers.
Suggested: What is Remote Desktop Protocol Attack and how to remain safe from it?
The Difference Between Spear Phishing and RDP Attacks
Phishing is a mass distribution hacking process in which the cybercriminal casts a wide net in the hope of making a few successful attacks. In a phishing campaign, the criminal doesn’t target victims individually but sends messages to hundreds of thousands of targets.
Spear phishing is more specific and targets a single individual or business at a time. In most cases, the hacker will approach you pretending to be a person you know or have previously dealt with. Spear phishing takes a more personal approach to breaching a network and eventually deploying ransomware.
What is Spear Phishing?
In spear phishing, the attacker is usually after one specific target. For example, in an email compromise scheme, the hacker may approach you as a senior employee with permission to request data on wire transfers, changes in direct deposits, or W2 data.
The attacker will use social engineering skills and impersonate someone you know to connect with you in a more convincing way. The scheme is accomplished by researching your contacts on social media or breaches in popular peer-to-peer protocols such as BitTorrent.
RDP attacks, on the other hand, involve Remote Desktop Protocol, a Microsoft technology that allows employees or people collaborating on the same project to log into remote workstations via the Internet. Each RDP endpoint is secured with a username and password, which can be vulnerable to brute force attacks or social engineering phishing attempts.
How to spot Spear Phishing attempts?
Spear Phishing, despite being highly sophisticated, can be spotted by anyone who knows the basics of email communication. The following screenshot is of an email that seems to be from the Netflix Payments Department.
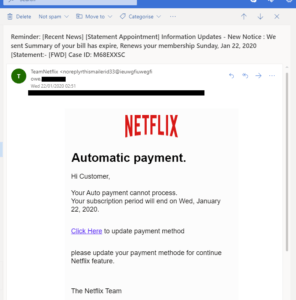
Image Courtesy of MalwareBytes Blog
But upon a close look, you’ll notice a number of hiccups:
- There are grammatical errors in the text.
- All emails pertaining to Netflix demand immediate payment or the account is threatened to be “closed.”
- The emails are all generic, without any personalization.
- The link points to a non https URL that did not belong to Netflix in any way.
Whenever you receive an email from a legitimate company, they always address you with your Full Name, and not a generic “Customer.”
But imagine if the tables are turned and the hacker is smart enough to outdo the receiver by using the following tactics:
- Breaching Netflix’s server to find out the full name of the customer
- Sending email from Netflix servers with a genuine link pointing back to Netflix
- Setting up an HTTPs address
Sure, no hacker goes this far to perfect their hacking strategy because unfortunately, a lot of people fall for this trick even in the first step. So if the hackers managed to outsmart everyone by perfecting their strategies and successfully stealing Netflix’s identity, even the most wary customer could fall in the trap.
That’s the difference between Nigerian Prince phishing, and Netflix spearphishing.
Protecting Yourself from Spear Phishing and RDP Attacks
Defense from spear-phishing attacks can be achieved through staff awareness and training. You can, for example, train all end users in your network to spot possible spear-phishing emails.
You could also invest in machine learning solutions that identify potentially dangerous emails, attachments, and malicious URLs. System administrators should also have in place all necessary security measures against malware on RDP endpoints.
It’s highly recommendable to disable the RDP service and close port 3389 when it’s no longer in use, use strong usernames and passwords, enable two-factor authentication, use secure Network Level Authentication, and have the most robust security software or solution.








