It is 10:00 PM on a Friday night, you are almost done closing up shop, thinking about your weekend plans, when you notice a strange message on your desktop. A ransomware attack often comes as a surprise.
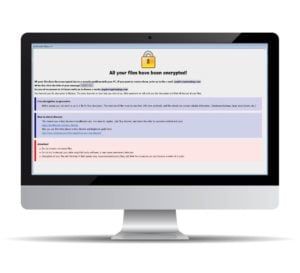
“All your files have been encrypted!”
“What? I just finished everything. Oh, it could just be another joke by my coworker!”
But something hits you! Instead of ignoring it, you randomly start checking files on your PC, noticing a strange set of extensions that just won’t open with any program, for example take the following screenshot:
Here comes the moment of brutal truth; your systems have been infected with ransomware and there is a high probability that your entire network is now compromised!
You are already stressed out, but note that no matter what you do, in the event of a ransomware attack, time is money! The quicker you notice and take action, the higher chances you have of saving your precious data. It takes time for files to get encrypted and potentially transfer over to the hacker for use in a leakware situation. Instead of panicking, remain calm and cycle through the steps mentioned herein.
What should you do in case of a ransomware attack? Our complete Ransomware First Response Guide will help you in minimizing your losses. This guide has been prepared by our experts after helping several of our clients based in Germany and worldwide come to a resolution and restore their operations after a ransomware attack.
Without further ado, the steps to follow:
Don’t panic.
Understand that your systems have been compromised. The ransomware attack has successfully managed to bypass all of your antivirus programs and firewalls. It is so sophisticated that the more you wait, the more damage it incurs. You now have three choices:
- Attempt to employ a free tool to recover your data
- Contacting the attackers and attempting pay them for decryption (which we do NOT recommend, and provide no warranties for any sort of ransomware data recovery)
- Restore from backup (The ideal solution!)
The first option is usually not feasible unless you have been attacked and had your files encrypted by and with an older variant which has had a freely available tool released. You can very quickly review the option of using a freely available decryption tool by visiting the following website: https://www.nomoreransom.org/
Important Note: Before proceeding with anything, take pictures of the entire process from your smartphone. You’re going to need them as evidence to report to law enforcement authorities.
Do you need to deal with hackers?
Going with the second option is a risky proposition. When you are dealing with a high stress situation, attackers take advantage of you and can greatly complicate the situation. There is no guarantee that you will see their promises kept and be able to recover your data. While we do not recommend engaging in communications with ransomware actors yourself and without professional help, it can many times be the only option.
It is important that you consult a ransomware removal company specializing in such incidents, such as BeforeCrypt. Dealing with the hackers and engaging in the proper due diligence for payment (as a last resort) should be done only by professionals. These hackers are very smart and shrewd, and present too much risk for anyone to deal with them without professional help.
Unfortunately, there is a vicious cycle in which businesses fail to invest properly in their security infrastructure and knowingly or unknowingly leave themselves open to attack, which could be more costly than having made an initial investment in prevention.
The FBI does not recommend nor prohibit victims of ransomware to pay a ransom. Here’s why:
“Paying ransoms emboldens criminals to target other organizations and provides an alluring and lucrative enterprise to other criminals. However, the FBI understands that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers.”
The FBI IC3 Public Service Announcement
The FBI, recommends that the businesses should have a solid prevention plan (such as training employees and sturdy prevention control methods) and a business continuity plan in the event of catastrophic data loss.
Ransoms are paid through Bitcoin or other cryptocurrency based payment and not a bank transfer. You also need to open an account at one of the legitimate websites to deposit funds and buy bitcoin, a process that could be time consuming. The following are the two of the most popular websites to buy and sell bitcoin:
Once purchased, and sent you have to keep in mind that the transaction is absolutely non-reversible, there are going to be no refunds, and you are on your own after paying the ransom.
Let professionals manage communication when there is no other option besides a negotiation. BeforeCrypt uses disposable email addresses, hiding the identities of our clients to reduce identity theft in the future.
Given that your company religiously makes backups and keeps them isolated from the network, you could have a good chance of recovering most of your data without any loss or sleepless nights. While a less than ideal situation, many companies choose to connect their backup systems to the network for real-time cloud backups. While convenient, the malware mostly focuses on spreading and encrypting backups BEFORE targeting any other system.
Inform your IT company
Many medium sized businesses and large enterprises have a dedicated IT department and they should hopefully already have a plan already in place!
Unfortunately, given budgetary constraints, many companies do not have an IT department in house. In this case, a third party managed service provider or IT company may need to call a meeting with the owners and staff to come up with a plan after the fact.
In instances like these, it is advisable to approach a ransomware removal and ransomware data recovery company that can do the job, such as BeforeCrypt, since having a specialized partner in handling such instances, saves time and avoids failure. An experienced company can help you save the day.
Time is money! Unplug your machines
When the patient is bleeding out, what do doctors do? They don’t treat the wound, rather they focus on first stopping blood loss, after which they proceed with treatment.
You never know, the message you just saw on your screen could very well be programmed to show AFTER all files have been encrypted, which may take hours or even days. Nevertheless, take no chances. The moment you notice the malware, immediately do the following:
- Disconnect all your drives from the network
- Power off wifi, bluetooth and ethernet cables
- If possible, power off the entire network by literally pulling the plug (without reckless abandon)
- Inform your remote workers who may be connected with the infected network to disconnect and shut down their systems
Find the root cause of the ransomware attack
Find the root cause, in this case, the first computer that got infected. It is not possible to have an entire network impacted by the virus simultaneously as it spreads from one system to the other and takes time.
We are living in the most challenging of times! COVID19, the novel coronavirus has forced economies to shut down leading to losses in the billions of dollars. Governments all over the world are focusing on controlling the root cause and isolating patients to reduce and/or eliminate its spread.
The case is no different when it comes to containing a malware attack. The cybercriminals are evil geniuses. Here are some of the ways malware is spread on through a network:
- When a coworker opens an email that looks legitimate, and downloads an attachment. Ransomware then installs on the system and connects with the command center of cybercriminals giving them complete remote access without your knowledge.
- A phishing email that looks legitimate and steals user login id and password. An example could be Google Accounts, Microsoft Outlook, standard chartered (or any other bank), etc.
Ransomware attack – Understand the type of ransomware
WannaCry. Does that ring a bell? It was one of the most dangerous ransomware attacks set out to trigger a mass blackout. By the time it was resolved, over 25% of the UK’s entire NHS systems were compromised, from systems to ventilators!
Every variant of ransomware is programmed differently, and hence treated differently. While there are myriads of strains for any ransomware, the two most common types are:
- Screen locking ransomware
- File encrypting ransomware
The screen locking malware is marginally easier to resolve and recover from as compared to the latter.
Ensure encrypted files are also backed up
Backing up encrypted files is an extremely important part of the process, soon after isolating the incident and discovering the ransomware variant you are dealing with, your next course of action should be to create a backup of all encrypted files. Once you have created a backup of the current state of affairs it is safe to move forward with ransomware recovery.
Decrypt or restore from backups? Ransomware attack recovery options
Once again, to save you much strife and further complication in an already incredibly stressful situation, it is advisable that you allow professionals to handle everything from possible communications, to payment and decryption of data in case of a ransomware attack. Based on our experience, the vast majority of recent cases of ransomware do not have any easy fix in the form of a freely available decryption tool. Hence, most of the time, it is the attackers that will send you a decryption tool. Paying the ransom on your own and waiting to get access to the tool for decryption is done at significant risk to the layman as there are no guarantees when dealing with criminals, not to mention not being well informed in regards to the structure, rules, and procedures of the ransomware gang you are dealing with, leaves you at a significant disadvantage.
We strongly encourage all victims of ransomware to report the incident to law enforcement. Please read our long form guide to ransomware response and recovery if you would like to be proactive about implementing optimal practices for prevention within your organization.
Are you going to pay the ransom or restore from backups? This is going to be the most challenging decision to make for your company. if you are lucky and have backups which have not been encrypted, it is worthwhile to take note of a few things:
- Ensure that you have the most recent information in the backup which is at your disposal
- Perform a test restore for 30 minutes to see the total time it takes to restore data
If you are restoring a few Gigabytes, it should be pretty straightforward and simple. For data stored in the Terabyte range, it may take several days depending upon the speed of your network and systems.
Significant damage has been done and you are in the final stages of data recovery. But before moving forward, you also need to perform a final assessment of the damages:
- Report the incident to the law enforcement authorities
- Use an Antivirus to do your best to remove any malware which may encrypt files proactively, if you are going to restore data to the same machine and environment.
In the instance that your most recent backup is too old, you have to choose between the loss of weeks or months of data and engaging in a recovery process which can be costly in both the sense of time expense and monetarily. Ensuring you continually have backups up to date is your responsibility. If your recent backup isn’t too old, and able to restore data during a 30-minute testing session, then you are better off in avoiding a recovery process.
Be transparent and communicate
If the nature of the data is of private and or personal relevance, such as usernames and passwords, you are legally obliged under the GDPR for Europe and potentially US laws, to communicate the data breach in the form of a press release/email to your colleagues and customers, including, but not limited to:
- The type of breach which occurred
- A date and time of breach
- A thorough damage assessment
- Any actions you have taken (such as paying the ransom, restoring from backups, reporting to the law enforcement authorities, etc.)
- Providing suggested actions to your clients (such as changing username/password, etc.)
Being transparent is important. While it is natural that your company will suffer due to the news of a data breach, the more proactive approach you take, the better it will be for the company.








