We’ve all read accounts of individuals and businesses getting locked out of their entire networks and being forced to pay a ransom to decrypt the data, or face their worst fear:
Watching hackers release confidential corporate and personal information into the wild!
But nothing happens overnight. Every single time you hear of hackers gaining control of the entire system, it doesn’t simply happen in one successful attempt. In fact, in order to penetrate an entire network, hackers rely on techniques such as phishing emails, etc.
In the case of phishing, you or an employee will receive an email be and asked to download and install a file, worse even still the attack can be completed through the simple aperture of a file bound with a payload which is executed through an exploit such as a buffer overflow among other things.
Once the intended action is taken by the victim, access is granted to the attackers and ransomware encryption is only a few clicks and commands away from being implemented.
Little did you know, that very file you downloaded and accidentally tried installing or very simply opened, contains a virus that gives hackers backdoor access to your website and/or network. To help you understand and prevent a ransomware incident we will be discussing several signs of a ransomware attack.
One of the MOST common methods of a ransomware attack is the exploitation of open links Remote Desktop Protocol (RDP) ports, through brute force and dictionary attacks
Over the course of the next few days or weeks for that matter, the backdoor remains open in the background without you even knowing it, logging all your keyboard strokes, other input, allowing malicious remote access and sending data back to the hackers.
It is through the RAT (Remote Access Trojan/Tool) and keylogger that hackers gain admin access, change passwords and eventually deploy ransomware encryption across the network, rendering any and all systems which are accessible in the attack, useless.
If a ransomware attack took place today, it usually means that hackers have gained access to the computer/network around a week ago.
As a matter of fact, there are signs of a ransomware attack immediately which can immediately point out the danger. If you notice any one or all of these, immediately disconnect from the network, call in your IT experts, and report the incident to your local intillegence agency and their cybercrimes division. Here are a few occurrences to take note of:
1. You get a ransomware notice
Out of all things that always happen in a ransomware attack, is a ransomware notice. Having been locked out of your system with critical information encrypted, and being presented a message demanding several if not, tens of thousands of dollars in Bitcoin payments, is no laughing matter.
Your system, is indeed infected with ransomware.
2. You get new installations of software you don’t recognize
While using any of the machines on your network, if you notice some sort of strange or weird looking software in the Start menu, a desktop shortcut or an unrecognized EXE file, it’s a wake up call! This is another one of many common signs of a ransomware attack and or impending ransomware encryption.
If you truly don’t remember installing any of it, immediately disconnect your system from the network and call in IT support to help you with the removal of malware along with a firmly recommended set of forensic testing and reports.
Remember, hackers never lock you out of your system on the first day! It takes them time, and you have a small window, perhaps about a week or so. Use it wisely!
3. Your computer is sluggish or slow to respond
If it takes ages to open a simple Word Doc file, then something is fishy. Windows PCs are notorious for bloating and slowing down over time, but all that takes place in a specific time period. It may take a year or so for your PC to slow down. But if you witness sluggish and/or poor PC performance, it’s time to run a scan, backup, format the hard drive and install a fresh copy of the Operating System.
Your system normally gets sluggish because of disk fragmentation, diminishing storage resources to be used as a swap, but we should be concerned about viruses and malware continuously keep track of your activities, and at times, maxing out CPU and RAM, which would definitely be the sign of a ransomware attack.
4. Scrambled or encrypted files
If you notice your data appended with unknown file extensions that you never remembered changing in the first place, it’s a clear sign of a successful ransomware attack.
Hackers deploy AES encryption to encrypt your data, which happens through the addition of a layer of cypher based obfuscation to binary data which composes files which changes the entirity of file content and file extensions, thereby rendering it totally useless to you.
Once you try opening up any encrypted file and you notice the following warning, you are compromised and a ransomware attack has been executed successfully:
Windows cannot open this file. To open this file, Windows needs to know what program you want to use to open it.
5. The Web Browsers are locked and encrypted
What happens when you need to browse the web? You use Edge, Chrome, Firefox, Opera or any other available browser.
When a challenge arises, the first thing that comes to mind is searching for the answer on Google!
But wait..you can’t seem to access your browsers and are consistently getting a notice:
Pay $13,000 in Bitcoin to this address to unlock your browser and files!
There you go! Nothing is a more glaring sign of a ransomware attack than a demand for bitcoin payment whilst opening up browsers!
6. An instance of MimiKatz running
MimiKatz is an open-source application utilized by hackers alongside Microsoft Process Explorer to steal user credentials. The moment you notice any instance of MimiKatz, immediately isolate from the network drives and turn off your systems.
You can stop the spread of the virus and a potential ransomware attack by simply doing this.
7. You receive instructions for ransom payment
A confirmed sign of a ransomware infection is that somewhere on Desktop, My Documents, etc. you will receive a text file containing payment instructions.
The file name starts usually with an underscore (_) and has the words in CAPITAL as if the gang is screaming at you for the payment of ransom!
8. You send and receive unknown mass emails
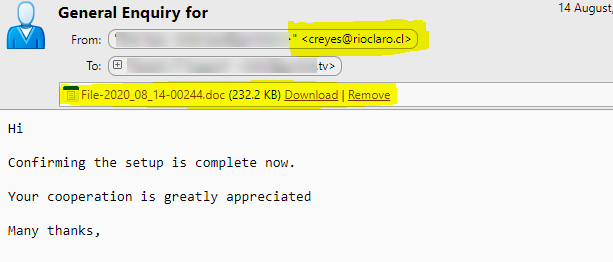
Here’s an example of how one of our clients was recently targeted in August 2020, of a phishing attack:
The email was sent from a legitimate address using a partner company’s infiltrated network, however the From address bar had a weird looking email address. This email was sent from the IT department giving an impression of an in-house attacker! Did you see that?
The doc file indeed was a virus and before it got downloaded, the issue was already highlighted by our experts.
9. Your computer keeps crashing frequently
When your idle resources start getting maxed out, such as CPU, and RAM, consider that something might be wrong. It means that the viruses left by hackers are doing their nasty businesses in the background, and keep crashing your system frequently.
10. Your Active Directory and domain controllers are disabled
Like we mentioned earlier, a ransomware attack doesn’t happen overnight. Hackers infiltrate networks and spend weeks in studying user behavior and the value of information before finally going all in and launching a ransomware payload!
Other than a splash screen and encrypted files, hackers will disable antivirus software, active directory and domain controllers, even not sparing the backup data on the network drives.
What to do in a ransomware attack?
A ransomware attack is incredibly dangerous, entire companies and corporations can shut down after suffering from huge data losses.
We have a detailed blog post on What to do in case of a ransomware attack if you want to find out more information on this topic. In a nutshell, here’s what you need to do:
- Disconnect your systems from the network, and if possible, shut them off.
- Disconnect your backup drives from the system.
- Find root cause of the attack.
- Assess the damages
- Do NOT communicate with the hackers under any circumstances.
- Call in an expert data recovery company such as BeforeCrypt to negotiate with hackers.
- Decide if paying the ransom is more economical than having the entire office shut down for weeks if not months.
Ransomware attacks aren’t going anywhere soon, and the speed at which they continue inflicting damages is likely to increase. Sorry to break it to you, but that is a rather inconvenient truth. We also do not advise you to simply rely on your antivirus software to prevent ransomware and much less, to provide ransomware recovery.
Remain vigilant! Keep an eye out for anything that looks or feels suspicious and always keep your antivirus systems up to date. Do not click any links in an email which is not clearly recognizable and has been expected.
If you follow the above guidelines, your chances of getting compromised and afflicted by ransomware will be very low.