What are Exploits and How Are They Connected To Ransomware?
Have you ever heard the term “exploitation”? Nobody likes to get exploited, taken advantage of, and then thrown away like a piece of paper! While we won’t be talking about emotions and relationships in this blog post, you get the idea, right? Exploits and ransomware, in their cybersecurity definition are described as:
Attacks by cybercriminals to take advantage of your system’s vulnerabilities with the sole intention of stealing your data and/or demanding a hefty ransom.
Exploits and ransomware. Aha! A match made in criminal heaven.
Now, do you get what we mean by exploitation? This is how criminals in the digital world take advantage of your system vulnerabilities. What could be a vulnerability? It could be anything such as not having an updated antivirus software installed, or even worse an expired software with no license renewal, or an open IP.
Anything that allows anyone with malicious intentions to take a sneak peak into your computer, is an exploit.
We shall be exploring how exploits and ransomware are connected with each other and how do these hackers take advantage of exploits to encrypt your data and demand a ransom.
On 23rd July 2020, Garmin, a US giant of smart wrist watches was hit by a massive ransomware, as a result of a system exploit that the company was hardly aware of. This resulted in much of the system going down for several days affecting all consumers trying to save their data.
Do companies patch exploits?
This goes on to show how companies as big as Garmin don’t take data privacy seriously. While most of the network is back up, it was an exploit that attackers took advantage of in injecting a ransomware. Some reports claim that the ransom demand was as high as $10 million, however the company refrained from commenting, which meant that Garmin must have paid an amount north of $1 million, as per our educated guesses.
It is impossible for a company to decrypt the data, and restore its activities in a matter of days. In case you don’t know just HOW IMPOSSIBLE it is, have a look at our recent post on AES vs RSA Encryption and the time it takes to decrypt the data!
Exploits are not in themselves a virus, nor a ransomware. It is basically a vulnerability through which ransomware, and malicious viruses enter your system and encrypt all the files for a heavy ransom. It’s like a lock that is easily broken by any intruder.
What are some types of exploits and how are they connected with ransomware?
Almost all types of exploits can be categorized into two types, known and unknown. Known exploits are the ones stored in an anti-virus software database, thereby detecting and stopping them before an intrusion takes place.
The unknown (also known as the Zero-Day exploits) have no records of use in the wild, are new, and pose a serious risk of files and systems getting compromised! While not 100% confirmed, we can safely assume that the recent Garmin attack which froze their entire network, was a zero-day exploit.
Since there is no software that can detect new zero day exploits, it becomes practically impossible to block them. As such, criminals and hackers mostly go with zero-day exploits to compromise governments and corporations!
Many viruses and ransomware variants are so sophisticated, that many of the TOP antivirus solutions fail to detect them and that’s how all hell breaks loose!
How do exploits occur?
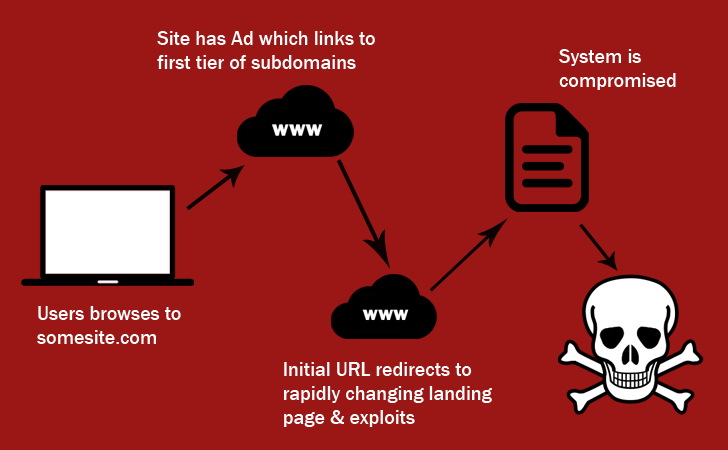
Source: How Hackers use Exploits to infect Ransomware?
There are a number of ways for attackers to use exploits, but the most common is phishing. The victim receives a seemingly legit email which contains a link to another seemingly legit website. The moment they click the link, hackers use the vulnerability to attack the system.
These phishing emails and/or malicious advertisements are mostly equipped with exploit packs, or exploit software toolkits. Most common victims of these attacks are outdated versions of browsers, unpatched software, Java programs, several free software such as PDF file readers, and browser plug-ins.
What are some protective measures to stay safe?
No measure provides 100% safety against malware, but you can adopt a series of protective measures to ensure hackers don’t take advantage of vulnerabilities:
- Just like you’d perform a routine inspection to check and lock the doors every night at your home and office, do the same with your computer. Its through open or poorly-closed doors (read exploits) that intruders take advantage of exploits to deploy ransomware. Keep your systems, files and antivirus software always up-to-date. Install security patches for your smartphone, or software the moment it gets available. The earlier you find and close these doors, the safer you’ll be.
- Install and update anti-virus programs with a complete firewall protection. These are important as they find known exploits in various programs such as Adobe software (PDF Reader, Photoshop, Premiere Pro), Google Chrome and several others applications with exploit vulnerabilities.
Conclusion
Exploits, once again, aren’t viruses, but they are often the starting point of attacks. Hence, it is important to use paid software and download/install only from reliable sources. Instead of going with an unknown browser “promising zero invasion of privacy”, go with browsers like Google Chrome and Microsoft Edge.
Do not click any link in an email. Companies like Google, Microsoft, IBM, Amazon, and Apple WILL NEVER ask you for your username and passwords. Just think about it for a second, why would they need to ask your credentials when they already have it all in their database?
Don’t share your username passwords with anyone, not even with your closed relatives. In no way use a public computer to access digital banking. You will always remain vulnerable of getting hacked. It is a continual race to security and we need to be ever vigilant to be best prepared and secured as possible against ransomware deployed through exploits.







